|
|
||
| Network Testing and Emulation Solutions |
| Opportunistic Key Caching (OKC) is a fast roaming solution that is one predecessor to 802.11r Fast BSS Transition. OKC is also referred to as Proactive Key Caching (PKC). Here we will demonstrate the following four scenarios with OKC: |
Using OKC on a VAP requires setting up a custom configuration file in LANforge to utilize the Multiple BSSID feature. In this scenario, the STA is not configured to use OKC and must do a full RADIUS authentication plus 4-way handshake when roaming to the next BSSID.
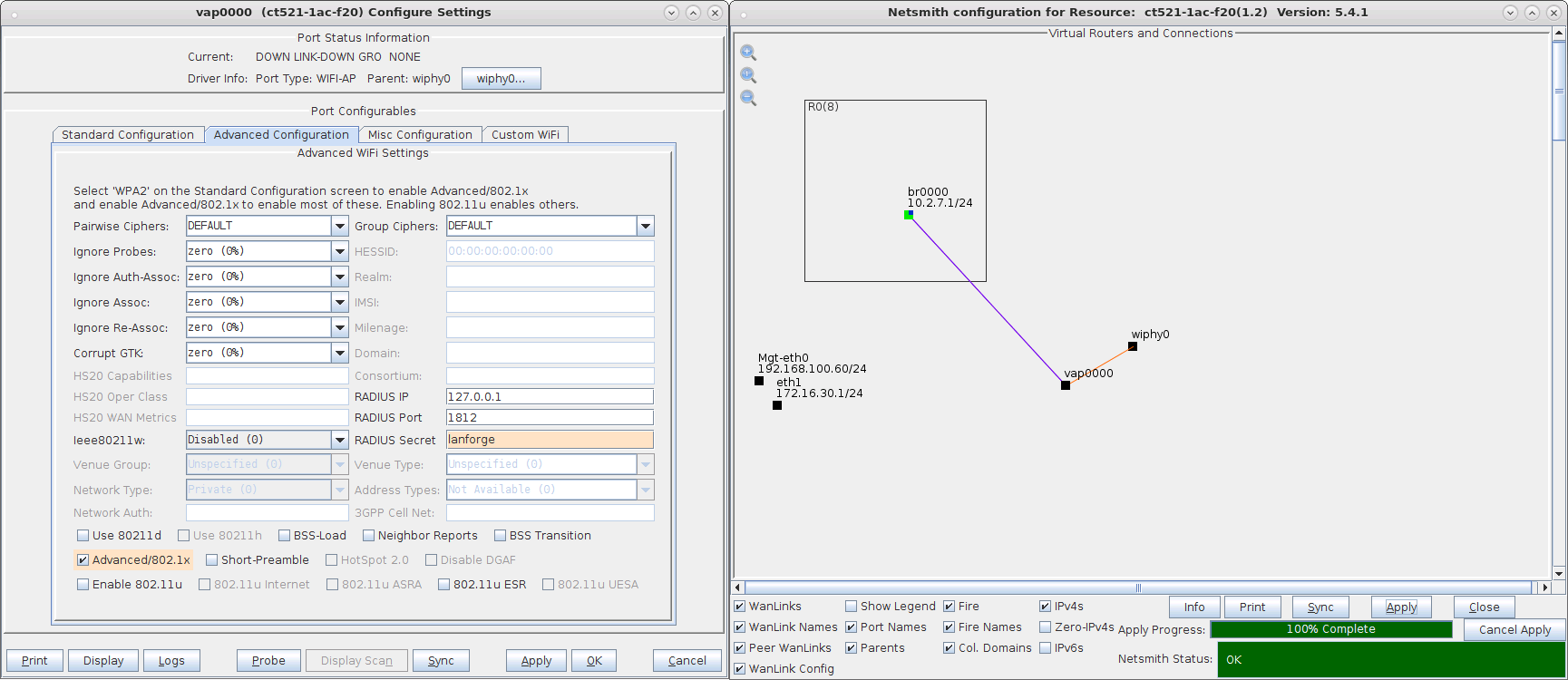
bss=vap0000_0 ssid=okctest1 bssid=04:f0:21:19:88:44 ieee8021x=1 own_ip_addr=127.0.0.1 auth_server_addr=127.0.0.1 auth_server_port=1812 auth_server_shared_secret=lanforge wpa=2 wpa_pairwise=TKIP CCMP rsn_pairwise=CCMP wpa_key_mgmt=WPA-EAP WPA-EAP-SHA256 bss_load_update_period=100 chan_util_avg_period=600 rrm_neighbor_report=1 rrm_beacon_report=1 bss_transition=1 okc=1 bss=vap0000_1 ssid=okctest1 bssid=04:f0:21:19:89:44 ieee8021x=1 own_ip_addr=127.0.0.1 auth_server_addr=127.0.0.1 auth_server_port=1812 auth_server_shared_secret=lanforge wpa=2 wpa_pairwise=TKIP CCMP rsn_pairwise=CCMP wpa_key_mgmt=WPA-EAP WPA-EAP-SHA256 bss_load_update_period=100 chan_util_avg_period=600 rrm_neighbor_report=1 rrm_beacon_report=1 bss_transition=1 okc=1
# cd /home/lanforge # . lanforge.profile # wpa_cli -i sta00000 scan # wpa_cli -i sta00000 roam <next BSSID>
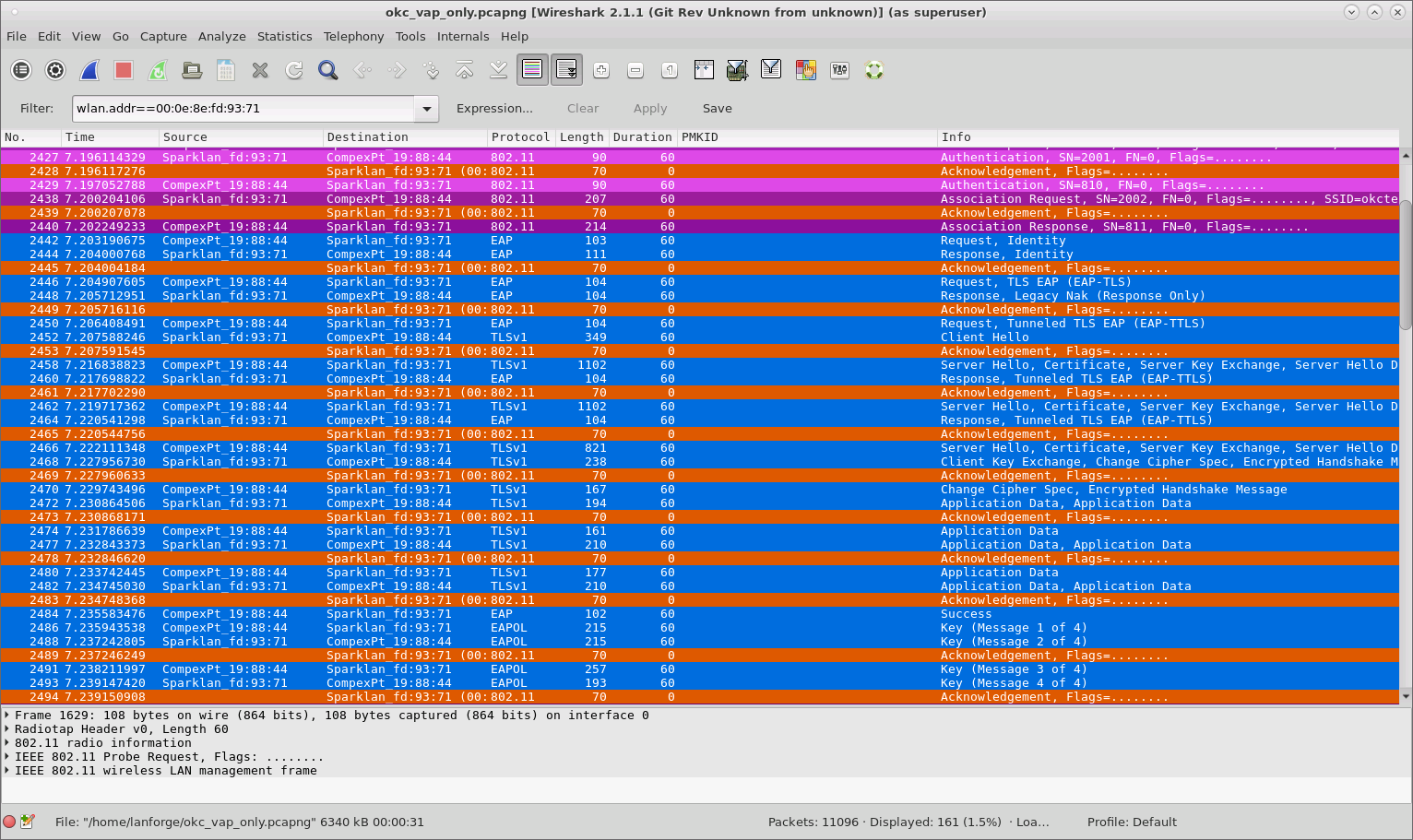
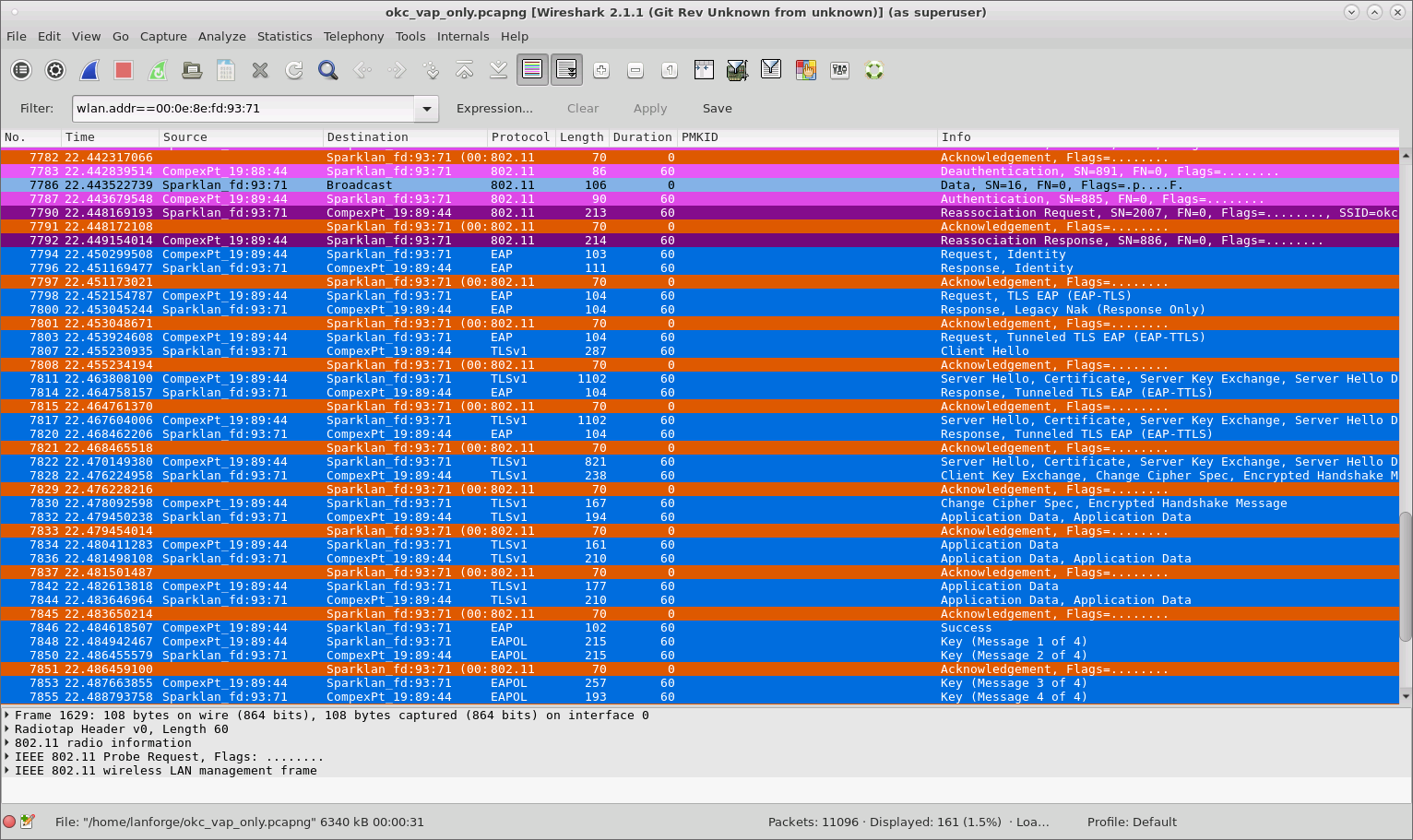
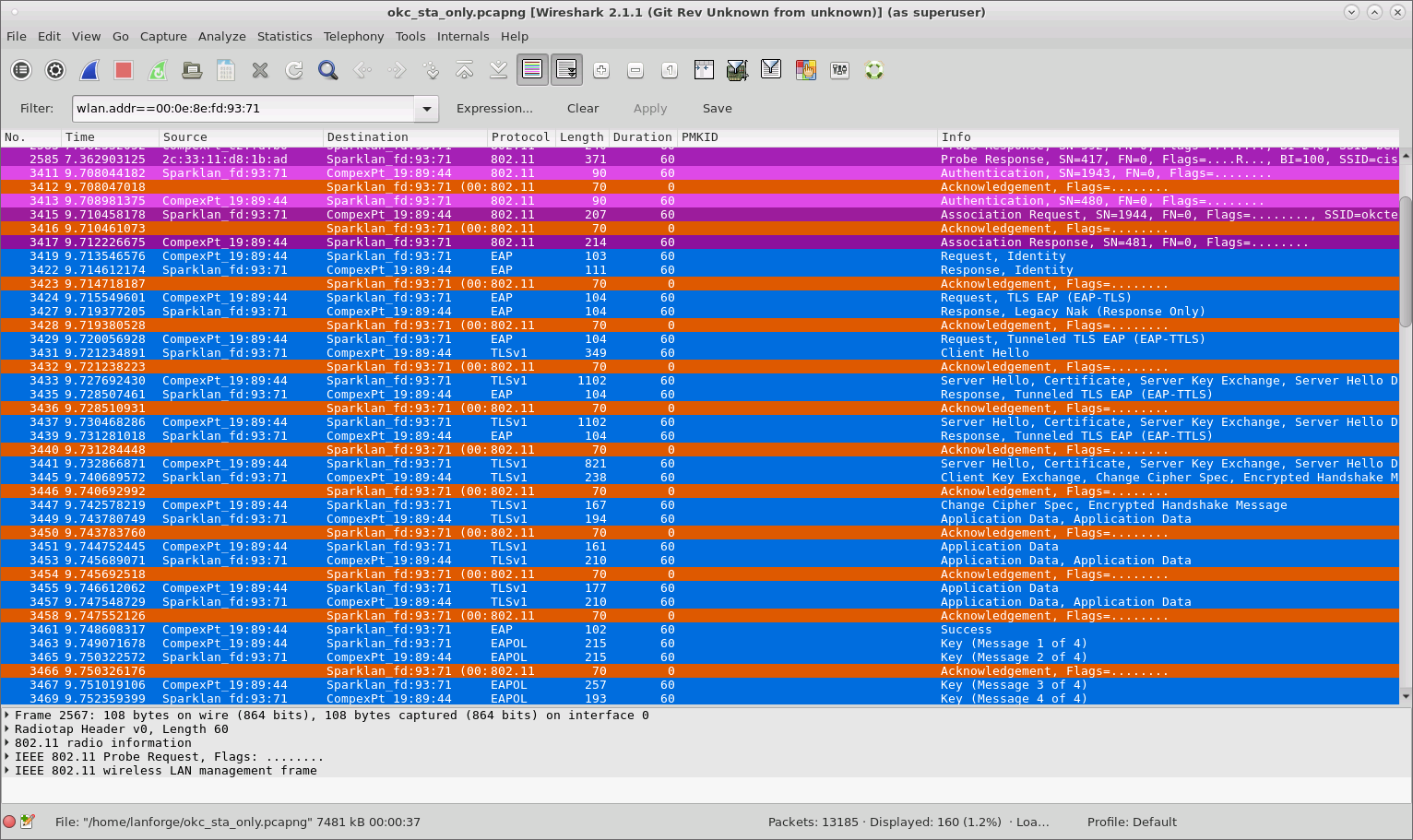
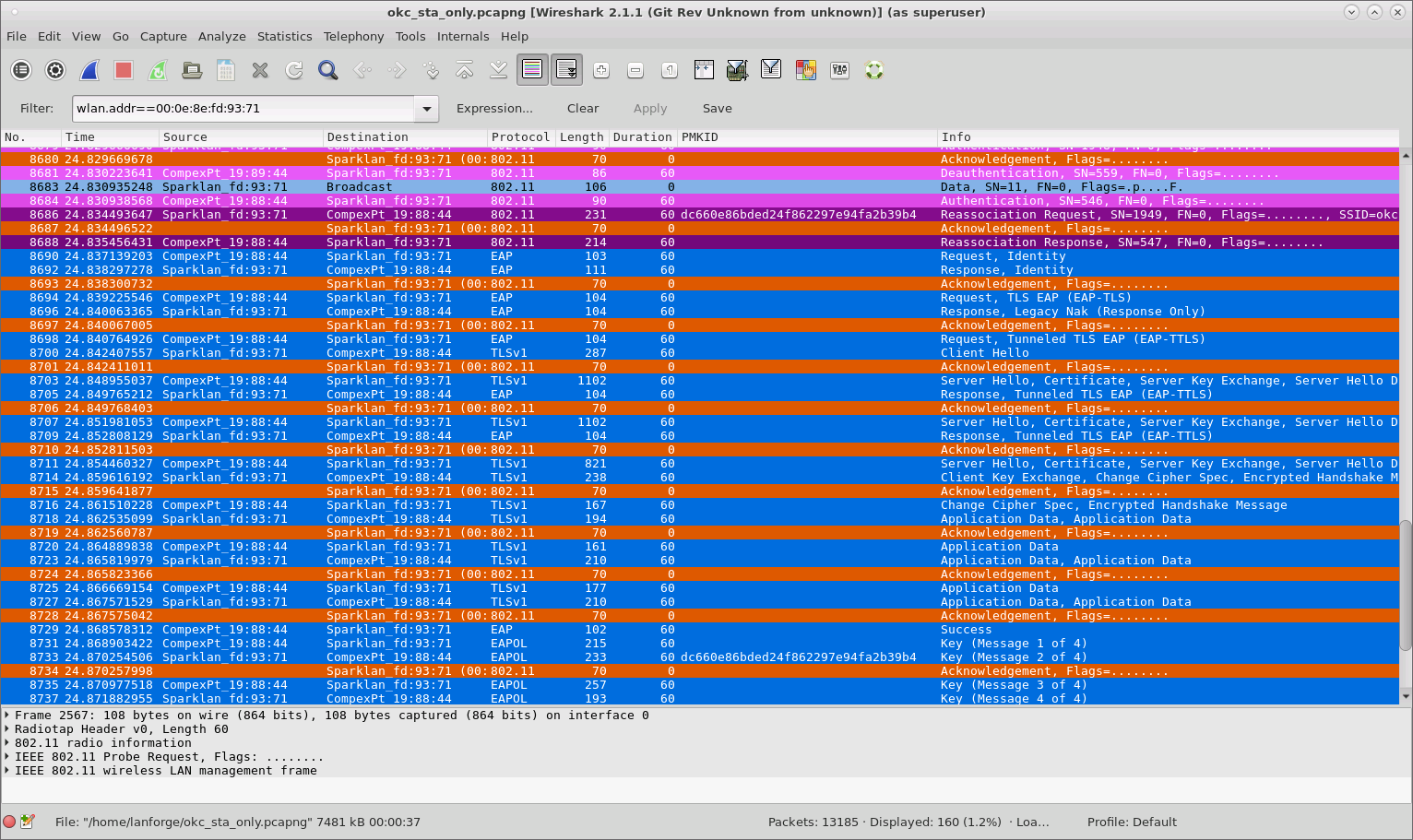
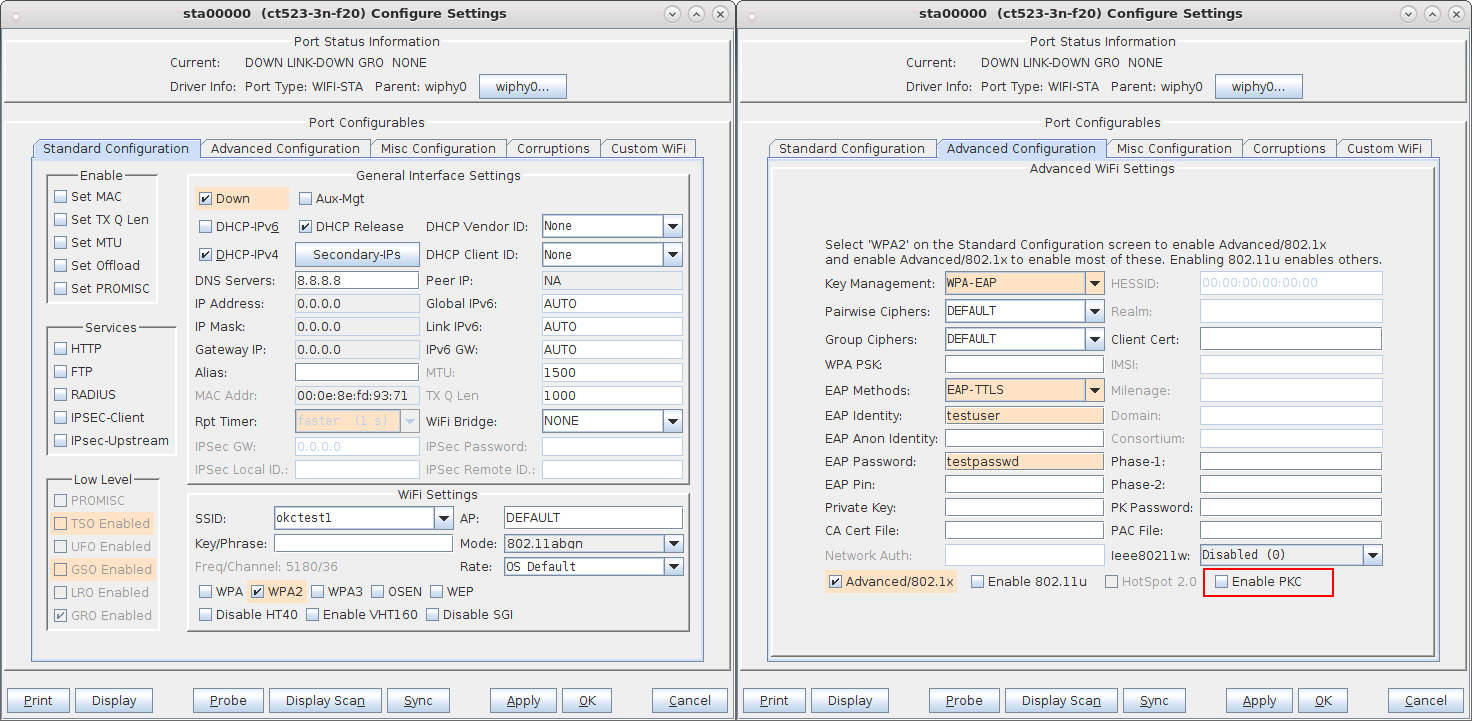
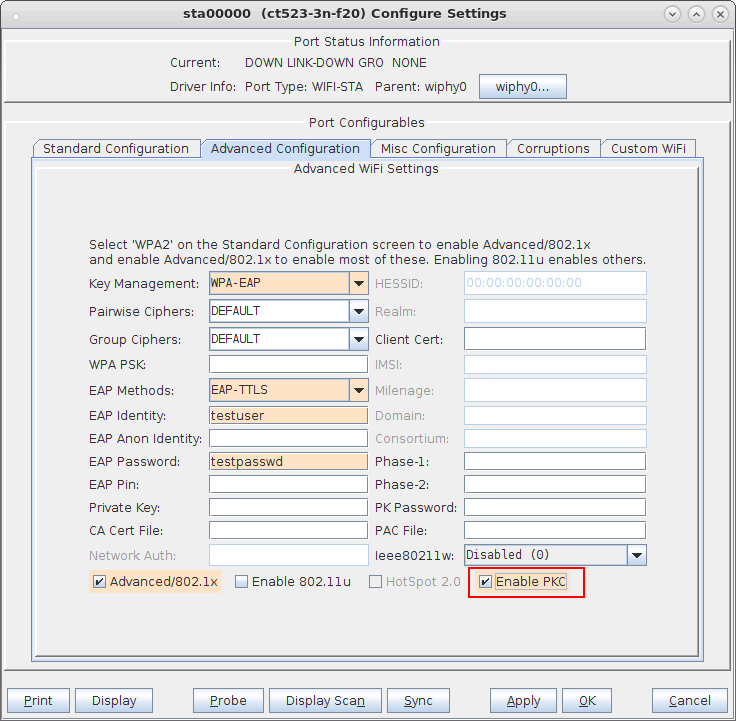
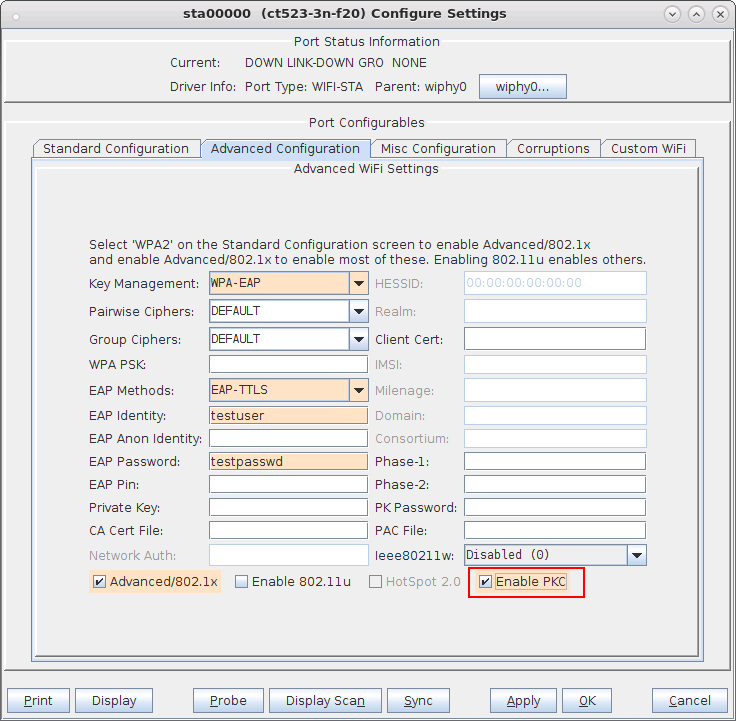
When both VAP and STA are using OKC, the STA sends its calculated PMKID in the Reassociation Request to the target AP which means the full RADIUS is not needed and only a 4-way handshake is sufficient to connect to the new VAP.
# wpa_cli -i sta00000 scan # wpa_cli -i sta00000 roam <next BSSID>
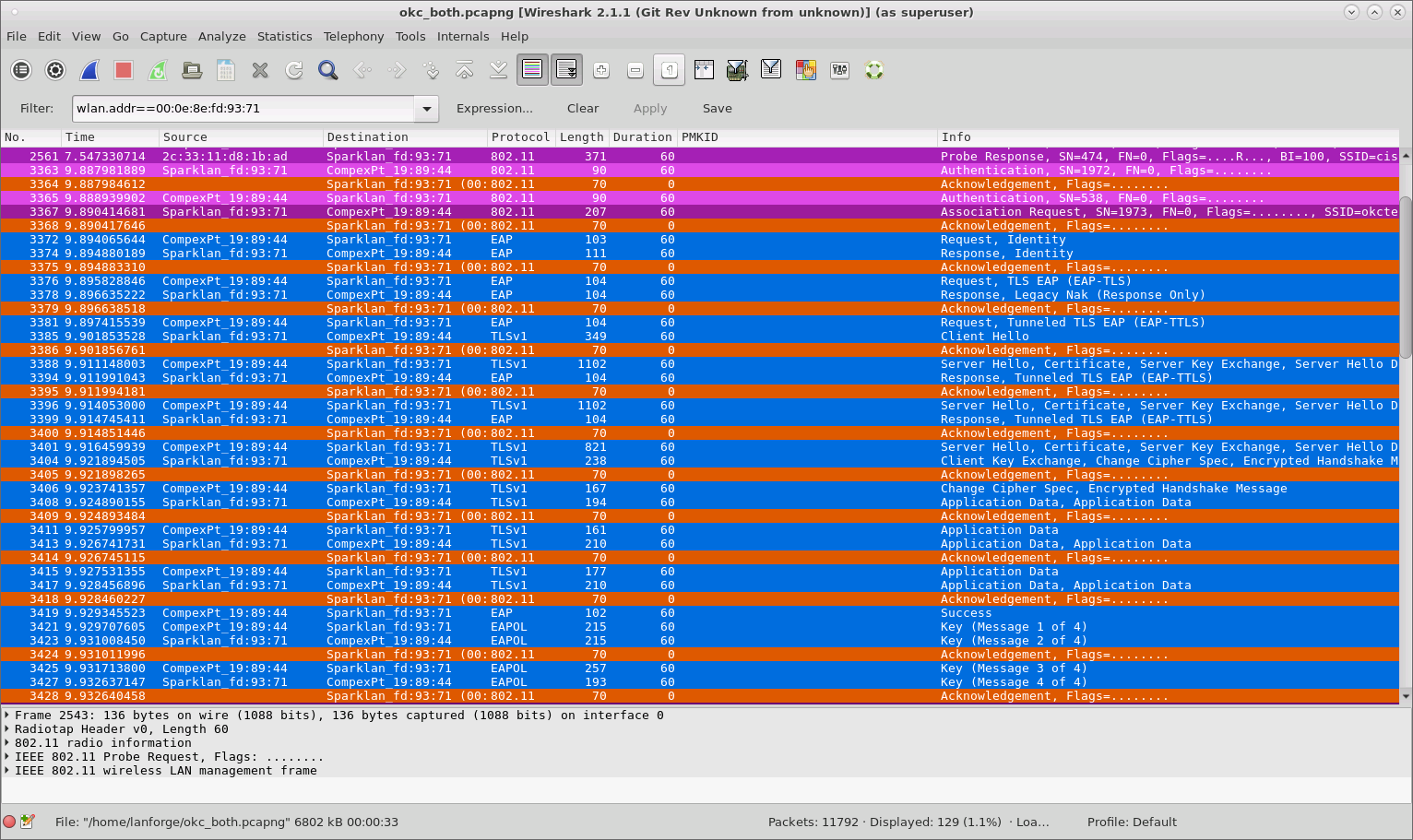
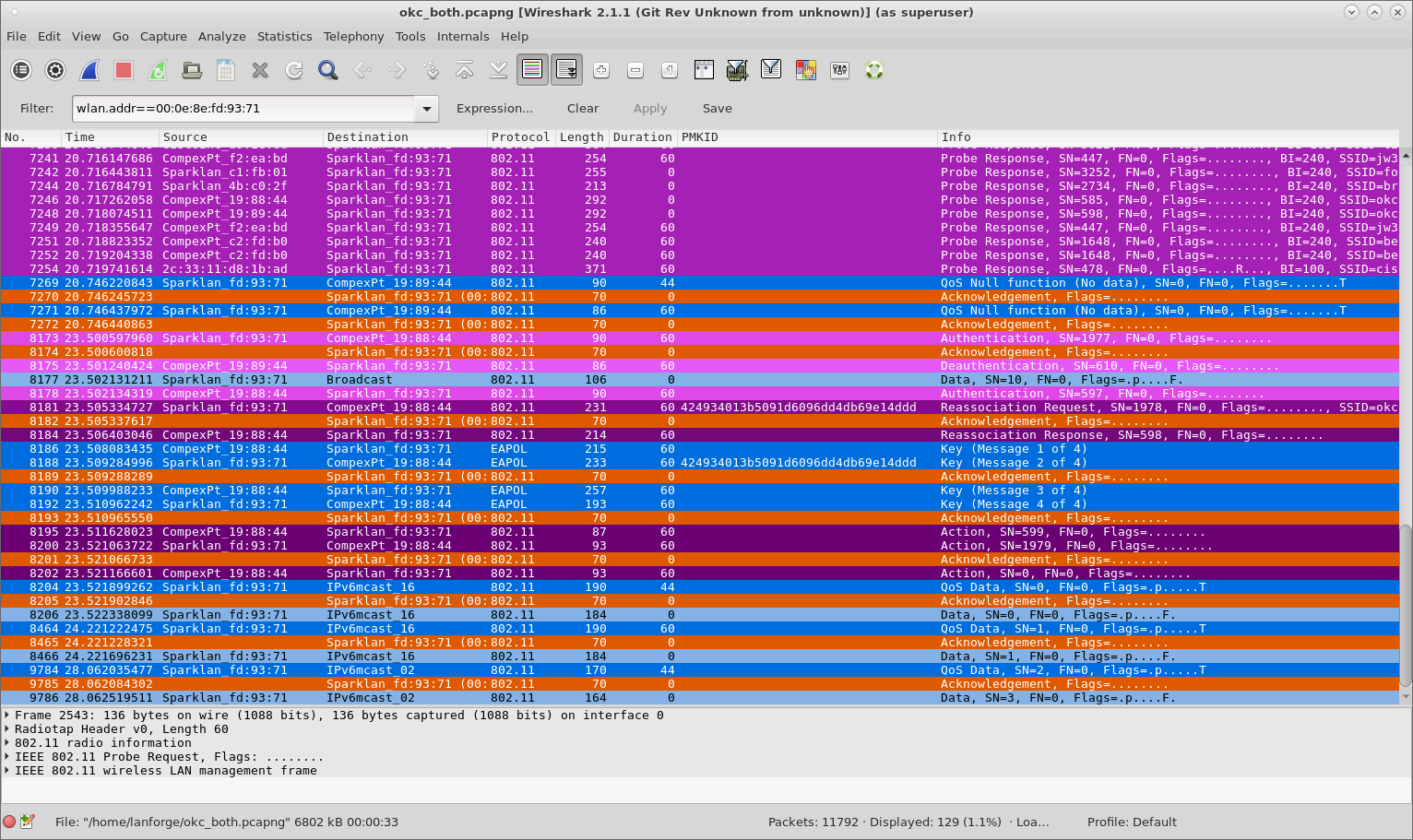
Because neither is using OKC, a full RADIUS authentication plus 4-way handshake is required when the STA roams to the new VAP.
bss=vap0000_0 ssid=okctest1 bssid=04:f0:21:19:88:44 ieee8021x=1 own_ip_addr=127.0.0.1 auth_server_addr=127.0.0.1 auth_server_port=1812 auth_server_shared_secret=lanforge wpa=2 wpa_pairwise=TKIP CCMP rsn_pairwise=CCMP wpa_key_mgmt=WPA-EAP WPA-EAP-SHA256 bss_load_update_period=100 chan_util_avg_period=600 rrm_neighbor_report=1 rrm_beacon_report=1 bss_transition=1 #okc=1 bss=vap0000_1 ssid=okctest1 bssid=04:f0:21:19:89:44 ieee8021x=1 own_ip_addr=127.0.0.1 auth_server_addr=127.0.0.1 auth_server_port=1812 auth_server_shared_secret=lanforge wpa=2 wpa_pairwise=TKIP CCMP rsn_pairwise=CCMP wpa_key_mgmt=WPA-EAP WPA-EAP-SHA256 bss_load_update_period=100 chan_util_avg_period=600 rrm_neighbor_report=1 rrm_beacon_report=1 bss_transition=1 #okc=1
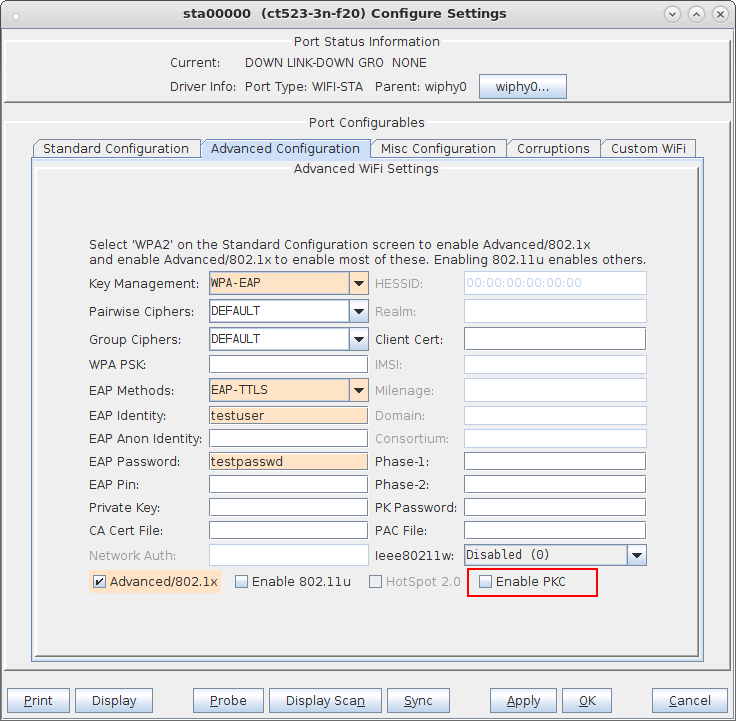
# wpa_cli -i sta00000 scan # wpa_cli -i sta00000 roam <next BSSID>
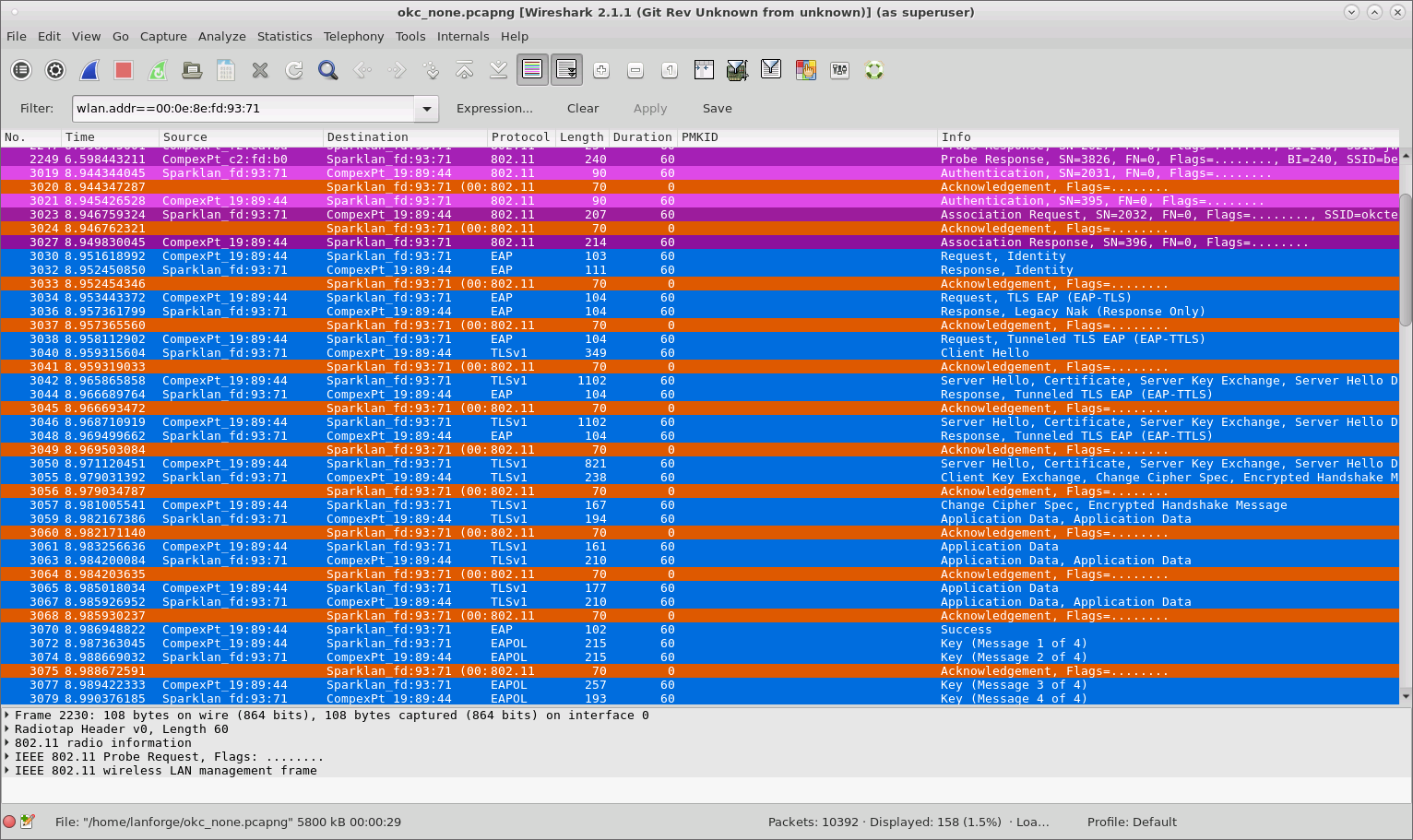
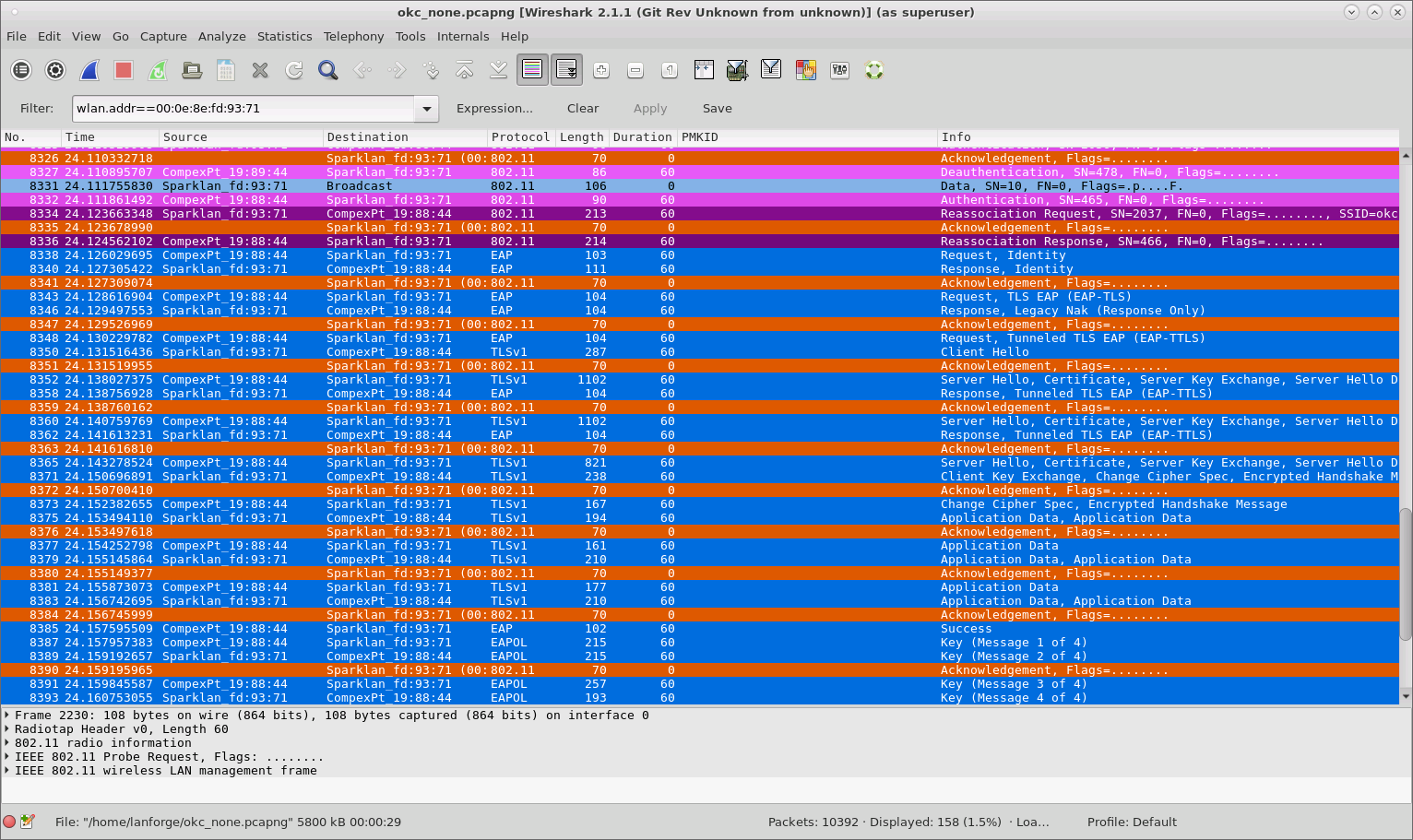
If just the STA is using OKC, it will send its calculated PMKID in a Reassociation Request to the target AP, but the AP ignores it and the STA must perform a full RADIUS authentication plus 4-way handshake.
# wpa_cli -i sta00000 scan # wpa_cli -i sta00000 roam <next BSSID>