|
|
||
| Network Testing and Emulation Solutions |
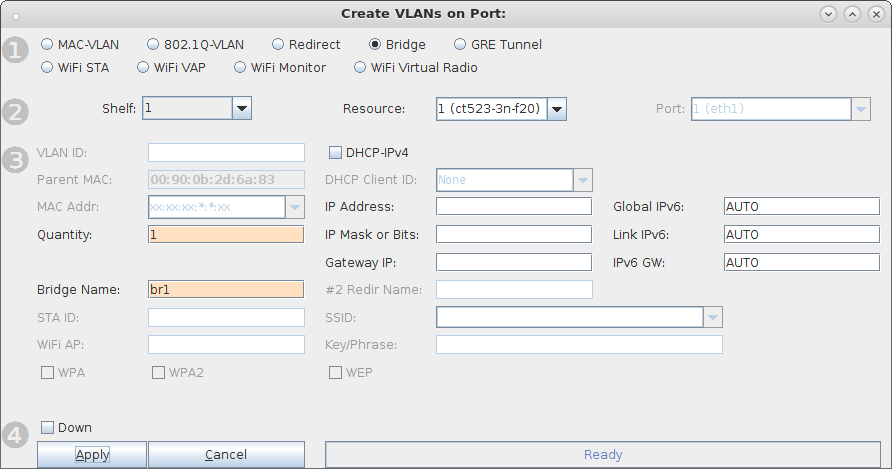
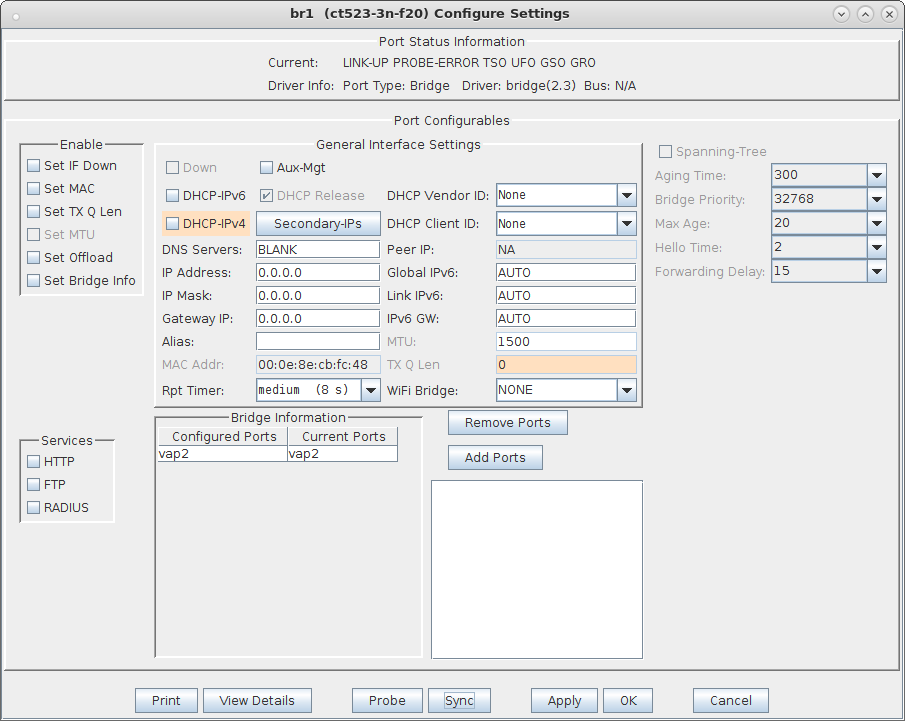
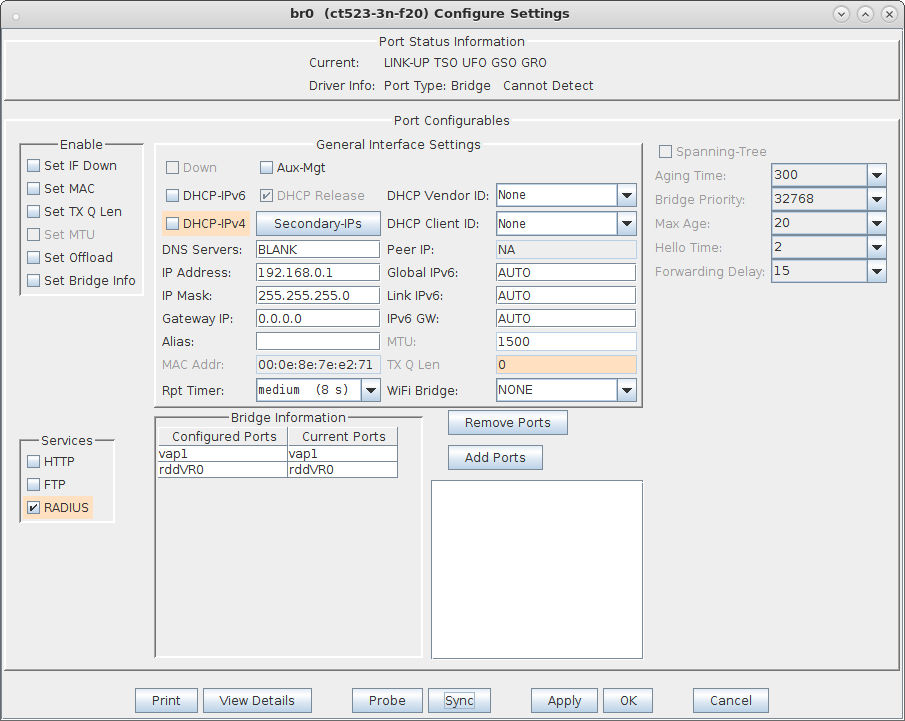
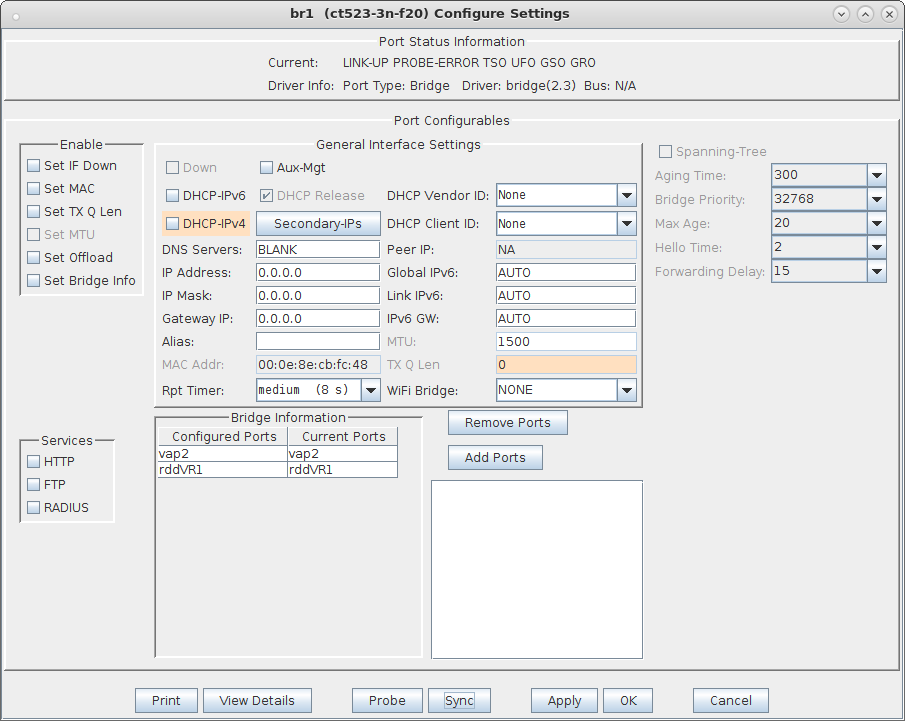
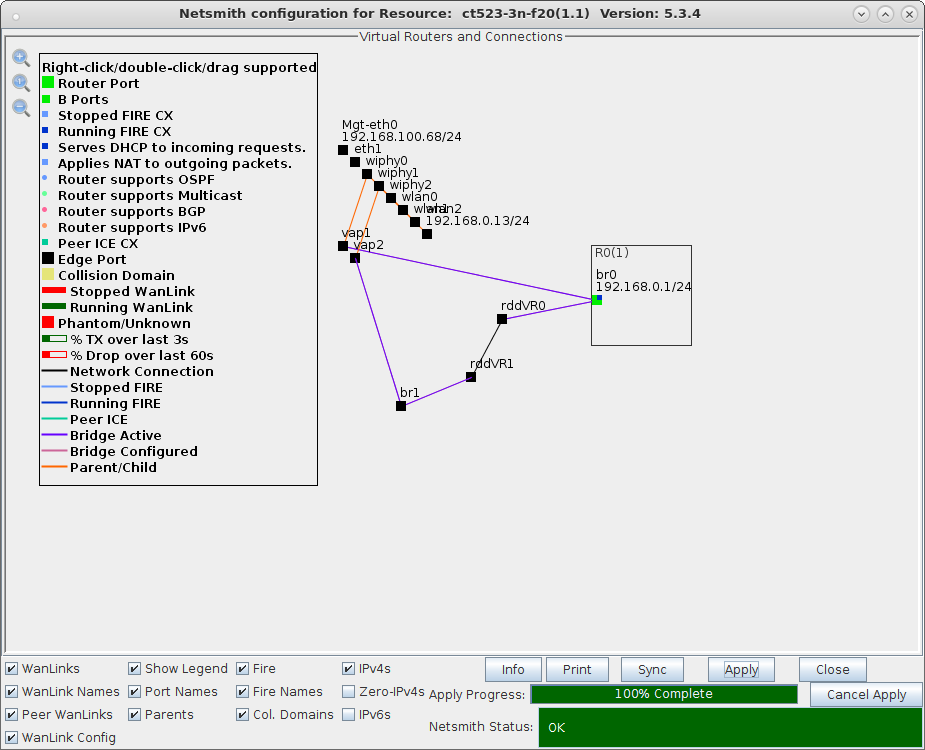
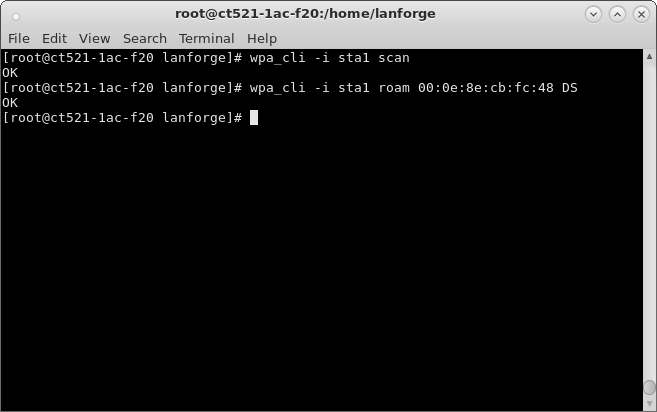
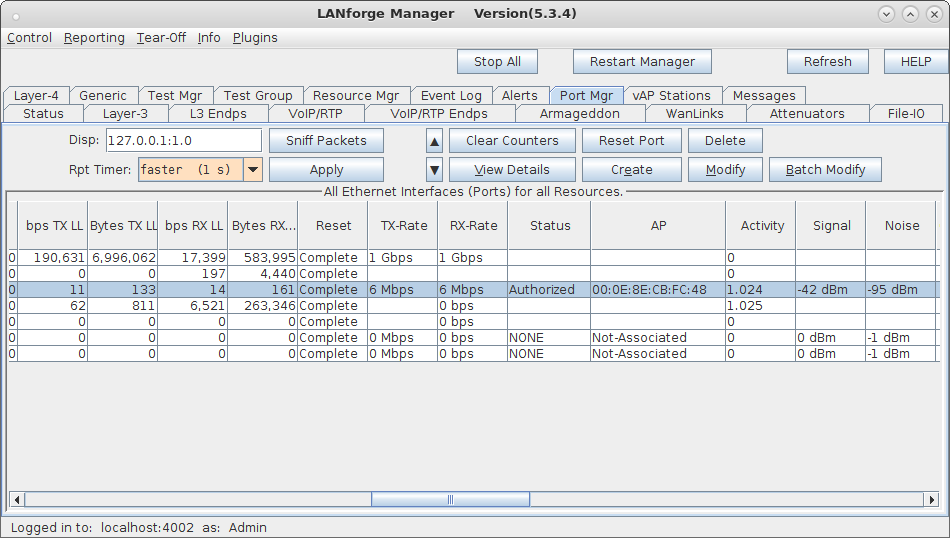
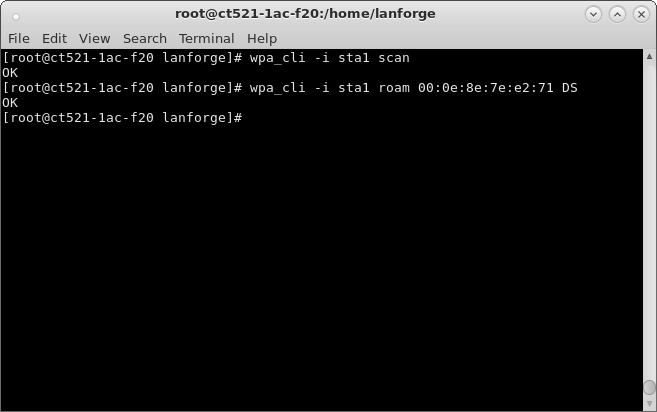
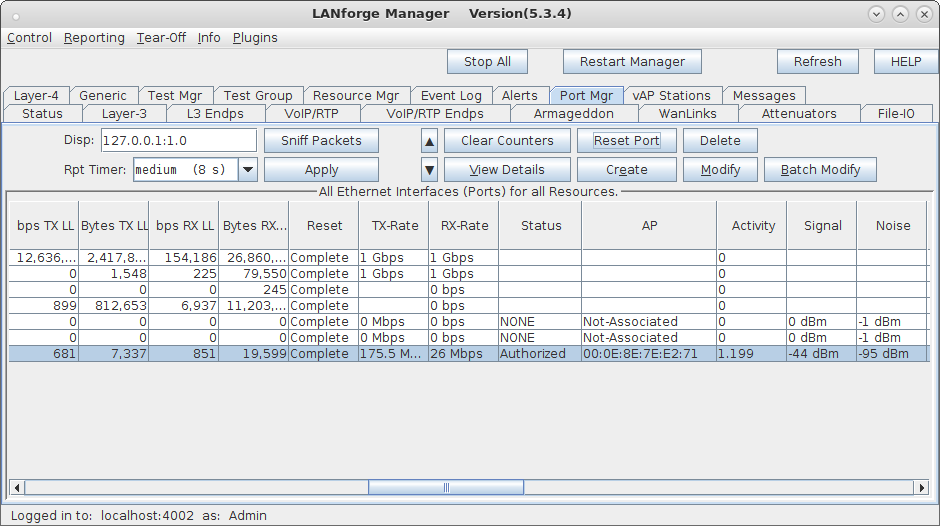
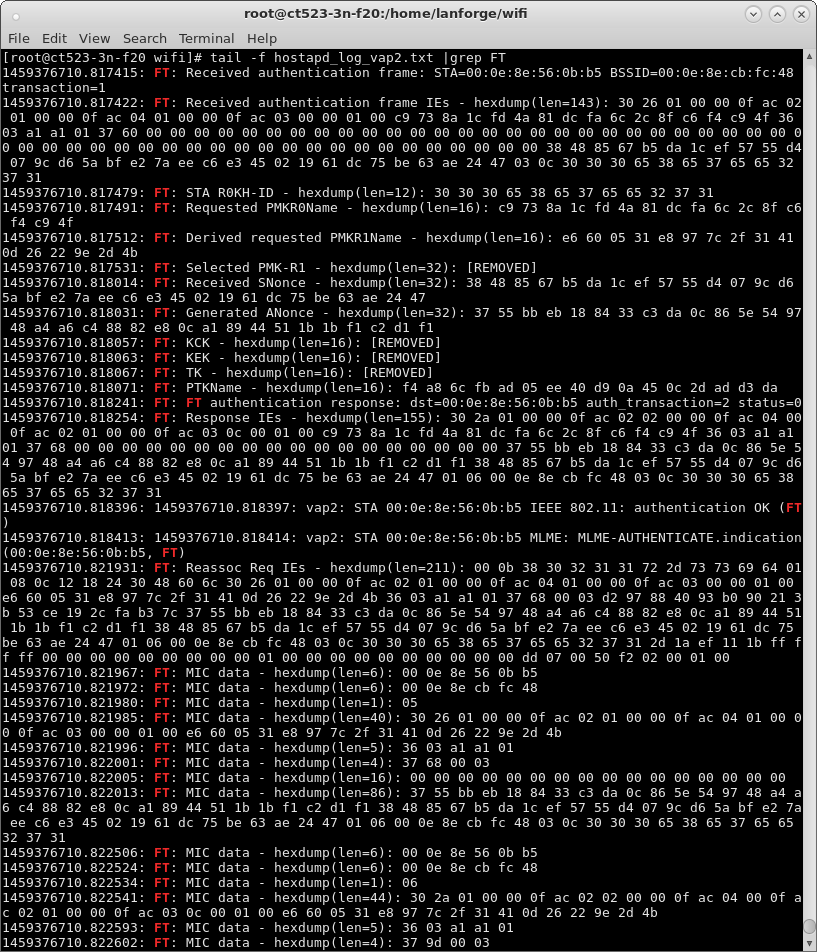
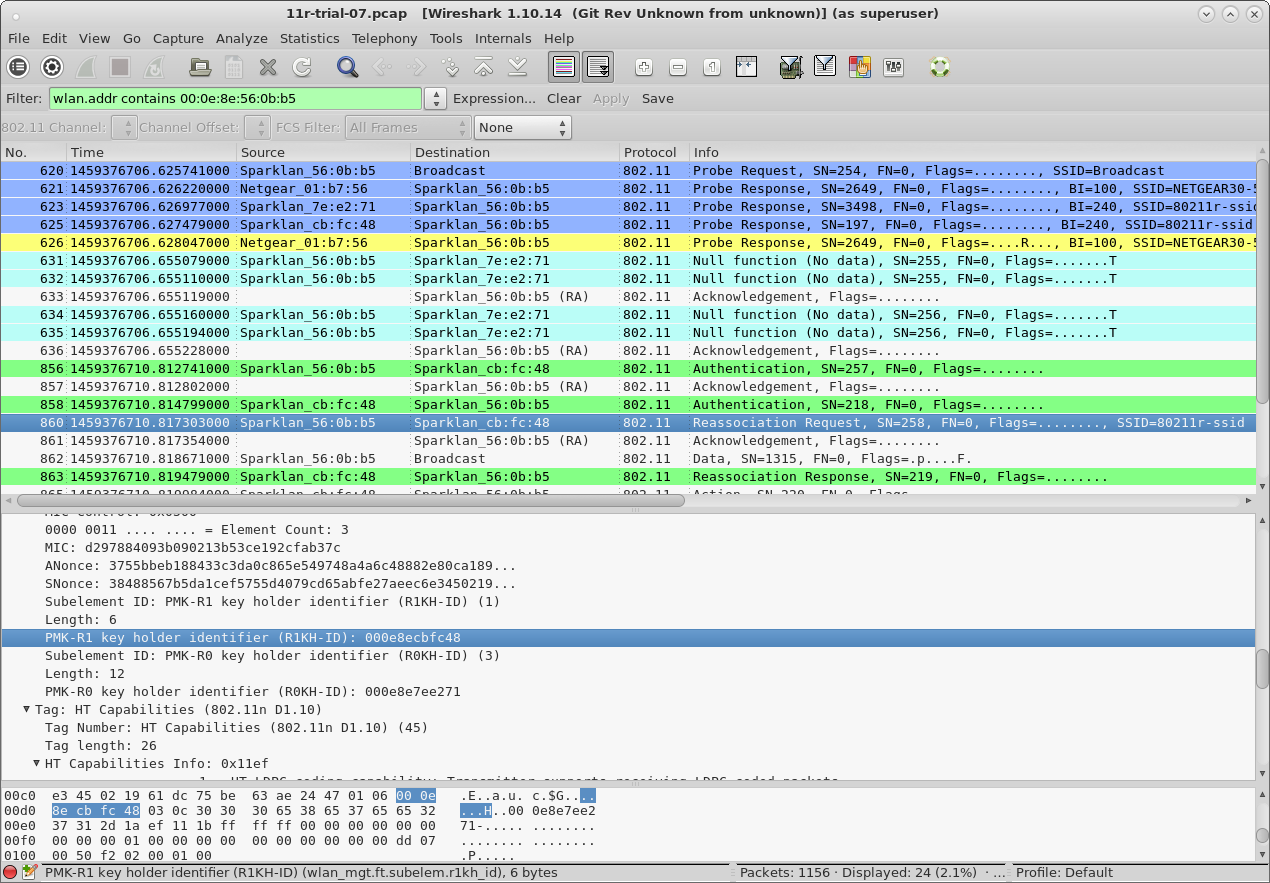
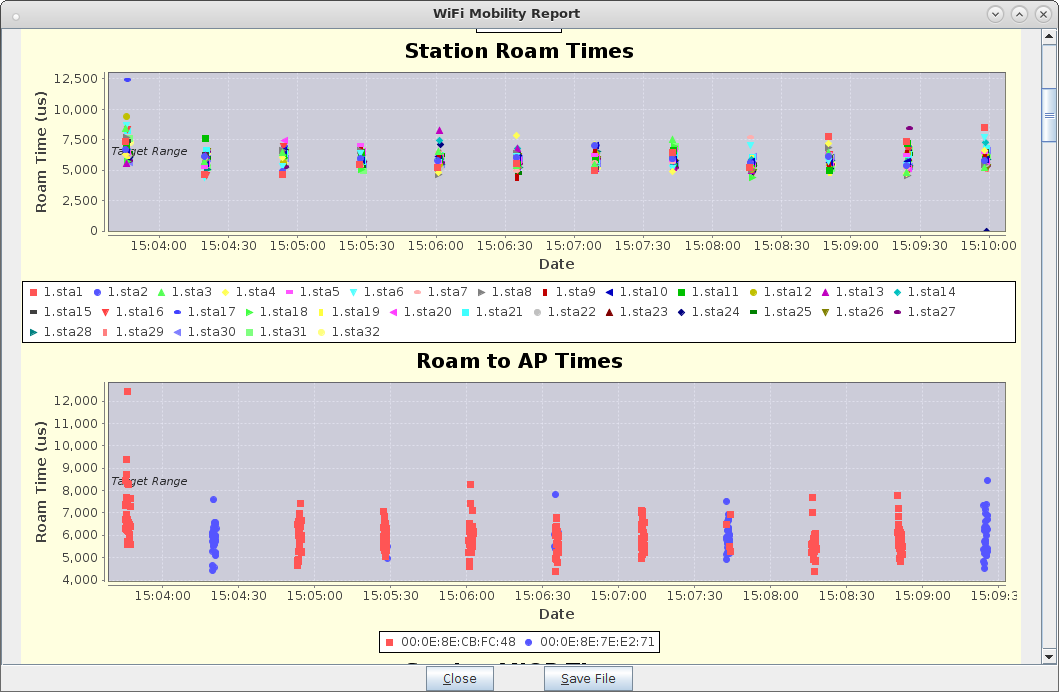
| Configure virtual Access Points to use 802.11r with FT-EAP. This example uses a LANforge CT523 system but the procedure will work on all CT522, CT523 and CT525 multi-radio systems. The wifi clients under test are also 802.11r enabled so that they can initiate FT Requests and roam. Here we are using another LANforge WiFire as the system under test to emulate 802.11r stations and force them to roam. In LANforge, each virtual access point will be running its own hostapd process configured to enable 802.11r and bridged to other virtual access points. The bridged VAP network will emulate the Distributed System (DS) for FT over-the-DS roaming. |

|
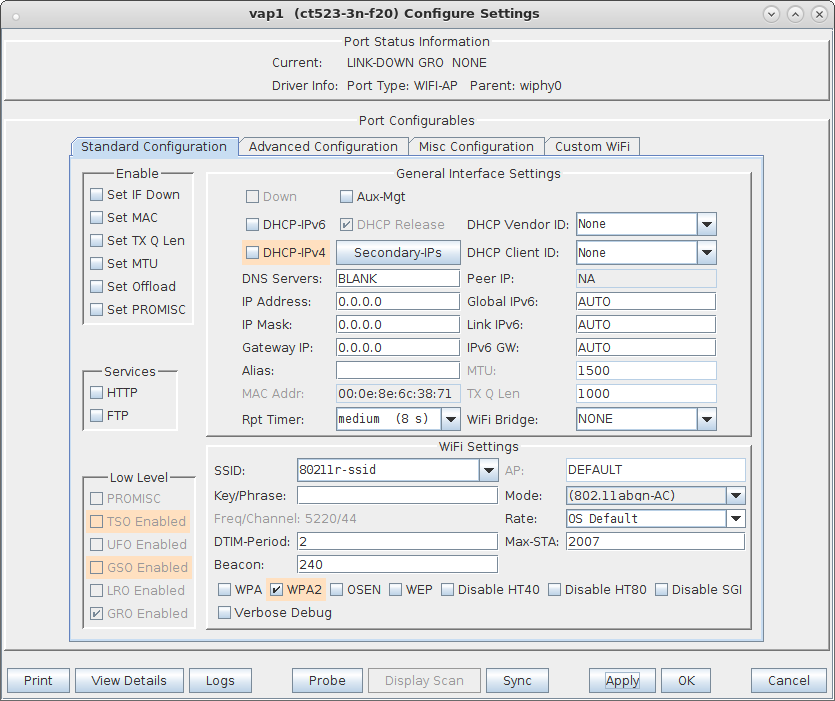
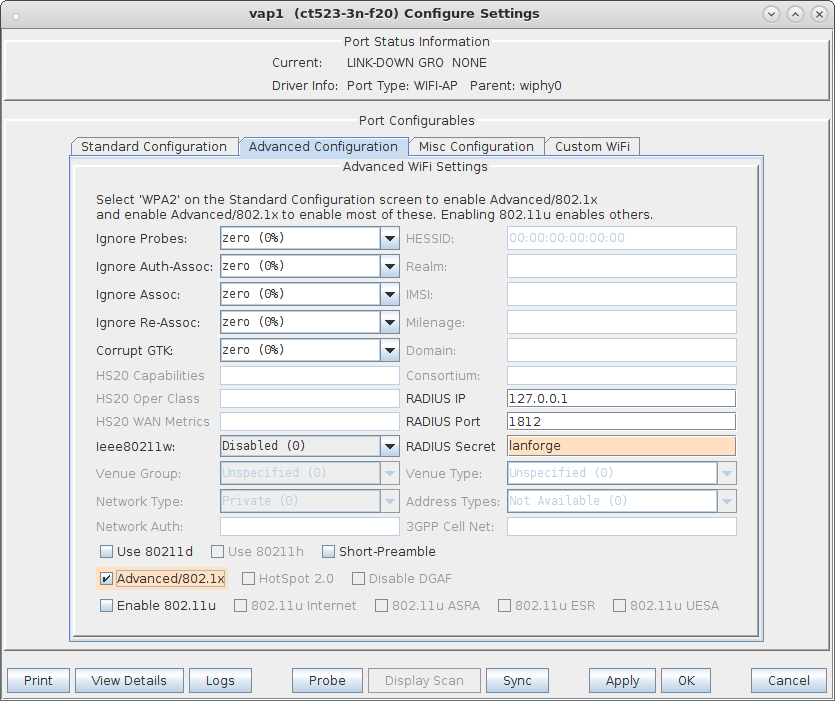
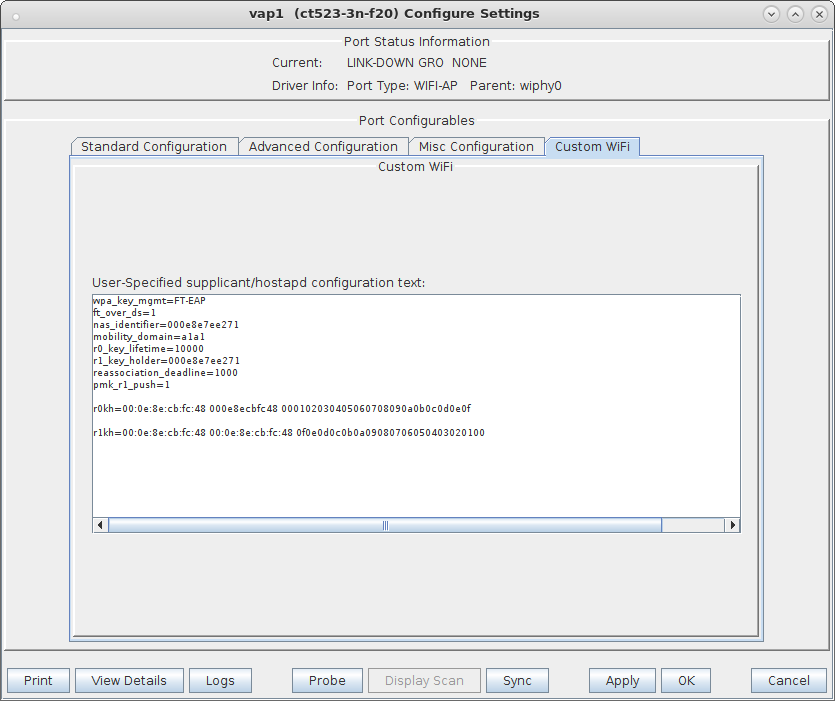
wpa_key_mgmt=FT-EAP ft_over_ds=1 nas_identifier=000e8e7ee271 #vap1 MAC without colon delimiters, yours will differ. mobility_domain=a1a1 r0_key_lifetime=10000 r1_key_holder=000e8e7ee271 #vap1 MAC without colon delimiters, yours will differ. reassociation_deadline=1000 pmk_r1_push=1 #r0kh is vap2 MAC address, vap2 nas identifier, AES key r0kh=00:0e:8e:cb:fc:48 000e8ecbfc48 000102030405060708090a0b0c0d0e0f #r1kh is vap2 MAC address, vap2 r1 key holder MAC, AES key r1kh=00:0e:8e:cb:fc:48 00:0e:8e:cb:fc:48 0f0e0d0c0b0a09080706050403020100full configuration file: hostapd_vap1.conf
wpa_key_mgmt=FT-EAP ft_over_ds=1 nas_identifier=000e8ecbfc48 #vap2 MAC without colon delimeters, yours will differ. mobility_domain=a1a1 r0_key_lifetime=10000 r1_key_holder=000e8ecbfc48 #vap2 MAC without colon delimeters, yours will differ. reassociation_deadline=1000 pmk_r1_push=1 #r0kh is vap1 MAC address, vap1 nas identifier, AES key r0kh=00:0e:8e:7e:e2:71 000e8e7ee271 0f0e0d0c0b0a09080706050403020100 #r1kh is vap1 MAC address, vap1 r1 key holder MAC, AES key r1kh=00:0e:8e:7e:e2:71 00:0e:8e:7e:e2:71 000102030405060708090a0b0c0d0e0ffull configuration file: hostapd_vap2.conf
wpa_key_mgt=FT-EAP FT-PSK wpa_passphrase=1234567890
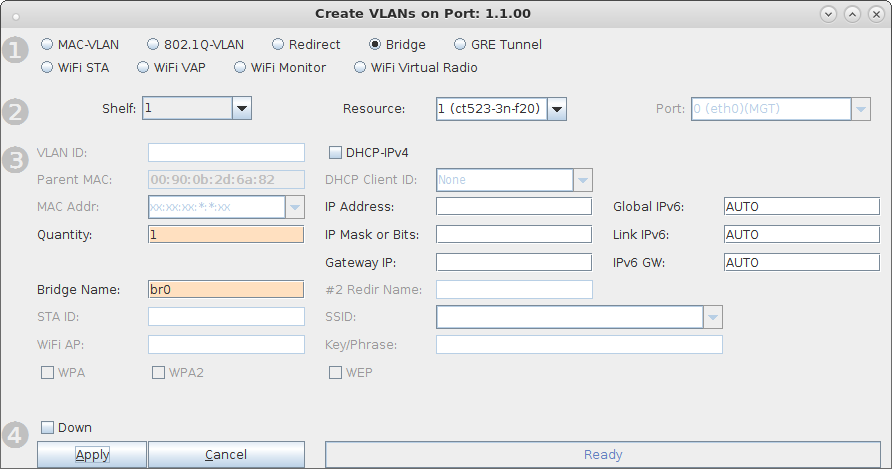
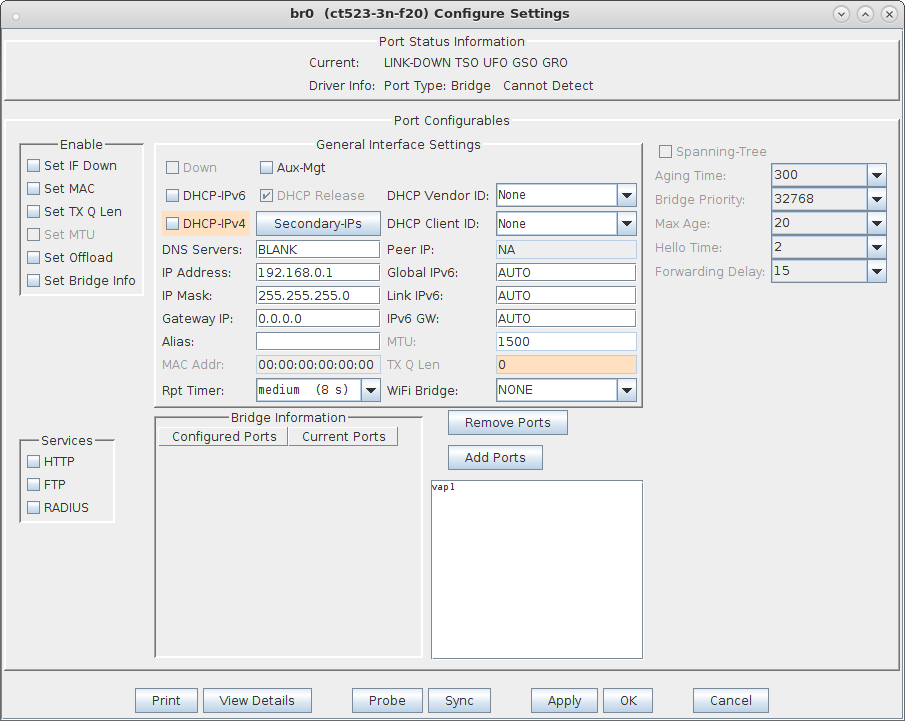
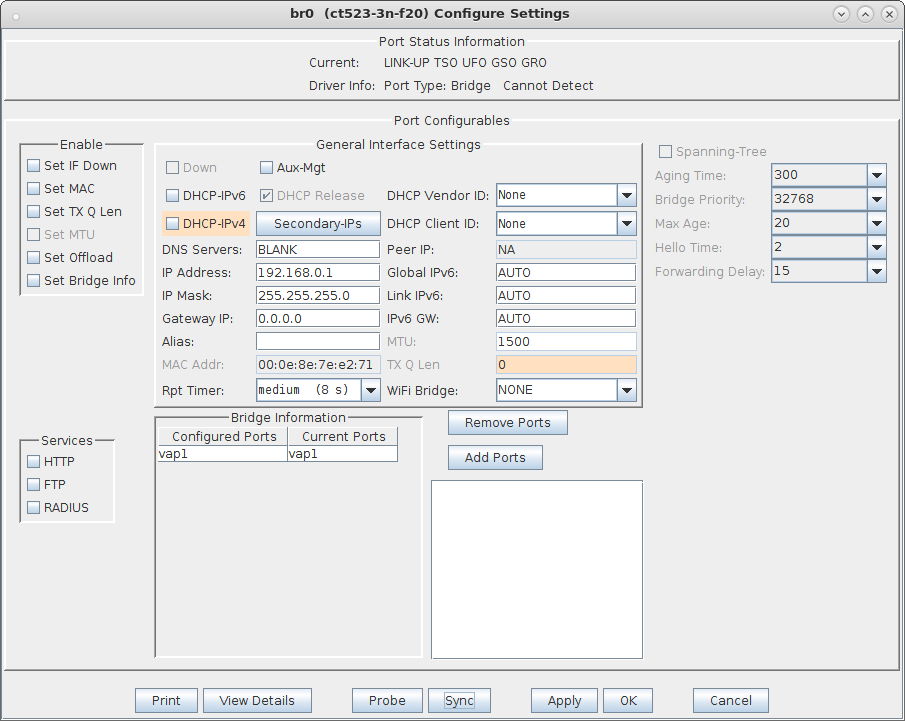
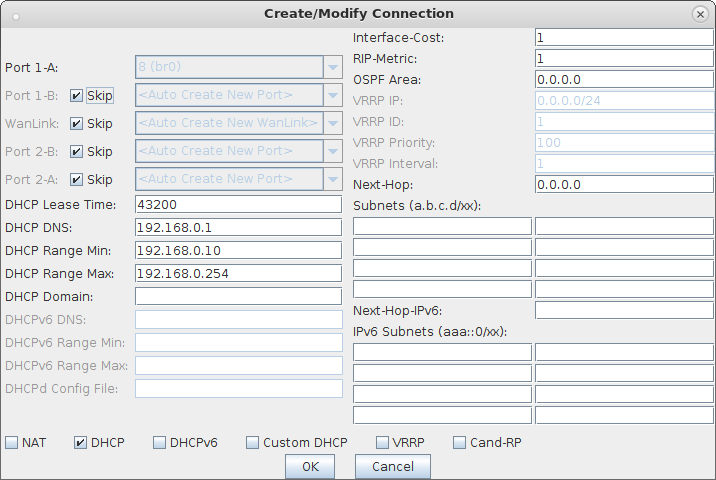
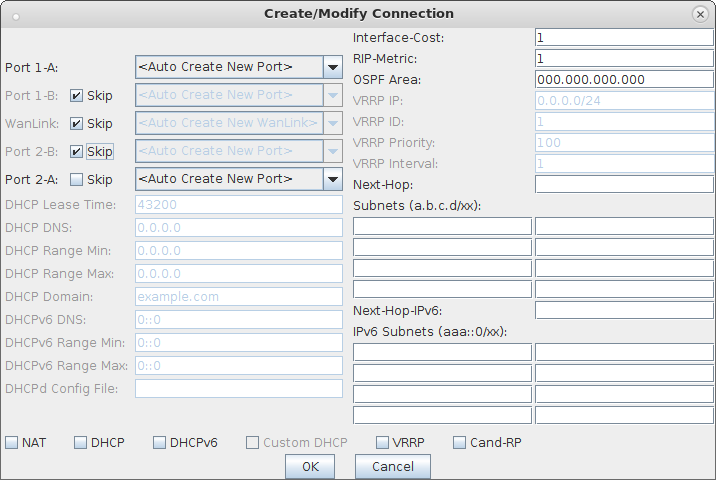
For more information see Virtual Router with DHCP Cookbook (skip the wanlink portion)
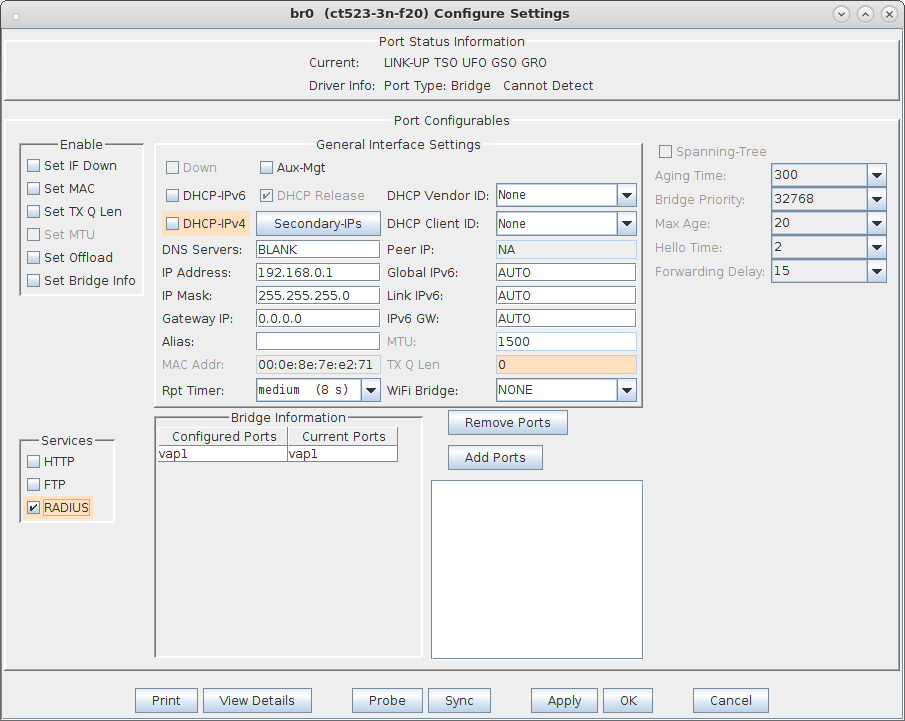
0.0.0.0/0 lanforge
"dot11r.user" PEAP "dot11r.user" MSCHAPV2 "!!dot11r123" [2]
interface=br0 driver=wired logger_syslog=-1 logger_syslog_level=2 logger_stdout=-1 logger_stdout_level=2 ctrl_interface=/var/run/hostapd ctrl_interface_group=0 eapol_key_index_workaround=0 eap_server=1 eap_user_file=/etc/hostapd.eap_user server_id=ct523-3n-f20 #Your server_id will be different. radius_server_auth_port=1812 radius_server_clients=/etc/hostapd.radius_clients ca_cert=/etc/raddb/certs/ca.pem server_cert=/etc/raddb/certs/server.pem private_key=/etc/raddb/certs/server.key private_key_passwd=lanforge
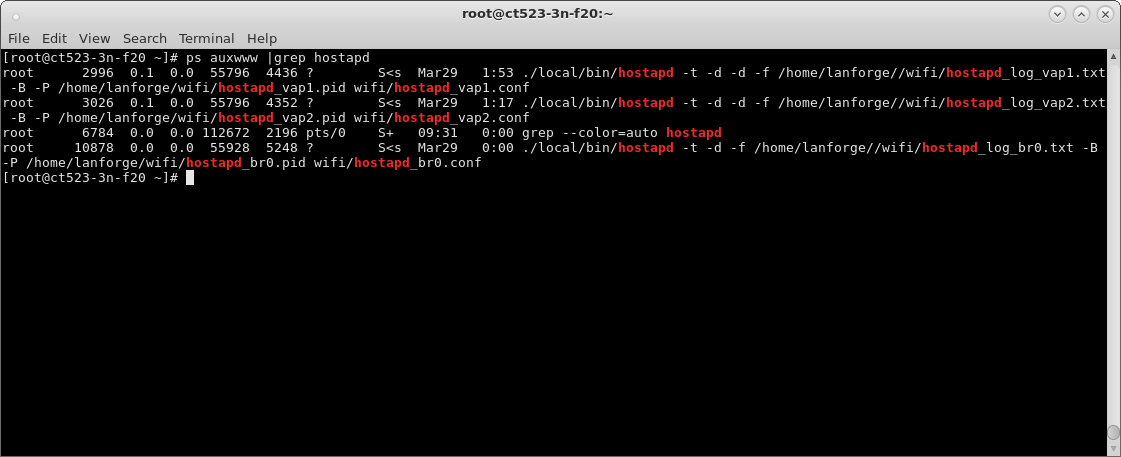
ps auxwww |grep hostapdwhich should show something similar to the following: