|
|
||
| Network Testing and Emulation Solutions |
Requires LANforge 5.4.2 or later on Fedora 20 or later (this example is using Fedora 27). VRF must be enabled (it is enabled by default). One LANforge system will be used as the AP side, and a second LANforge machine will be the WiFi station.
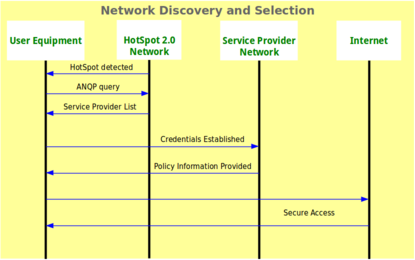 For more information see: WiFi Alliance Passpoint Release 2 Deployment Guidelines https://www.wi-fi.org/file/passpoint-release-2-deployment-guidelines |
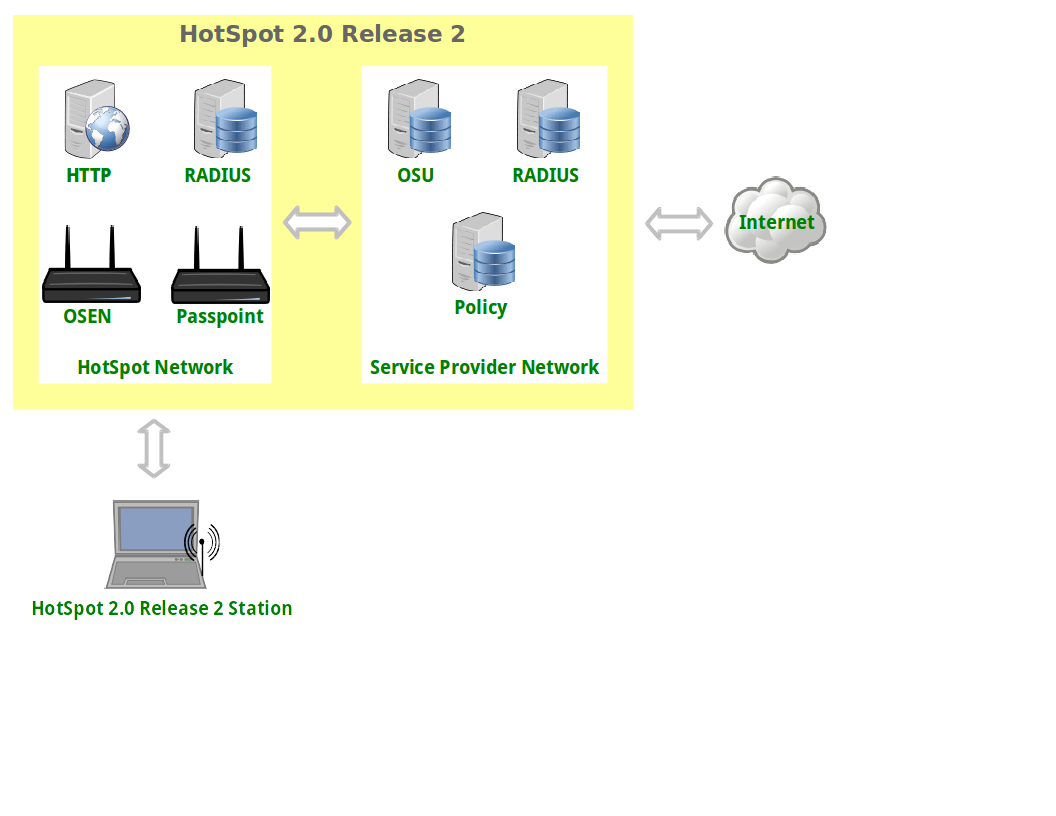
|
cd /home/lanforge ./lf_kinstall.pl --do_radius --do_hs20 --force_new_certs
cp /home/lanforge/hs20/ca/ca.pem /home/lanforge/osu-ca.pem cp /home/lanforge/hs20/ca/ca.pem /home/lanforge/ota-ca.pem #On station machine, if different from AP machine cp /home/lanforge/hs20/ca/ca.pem /home/lanforge/wifi/osu_wlan2/osu-ca.pemota-ca.pem is used by the client for Over-The-Air authentication to the OSEN AP
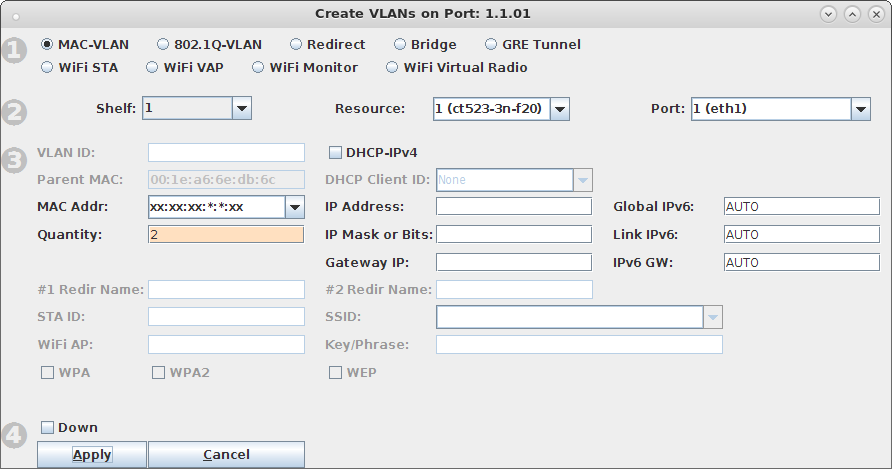
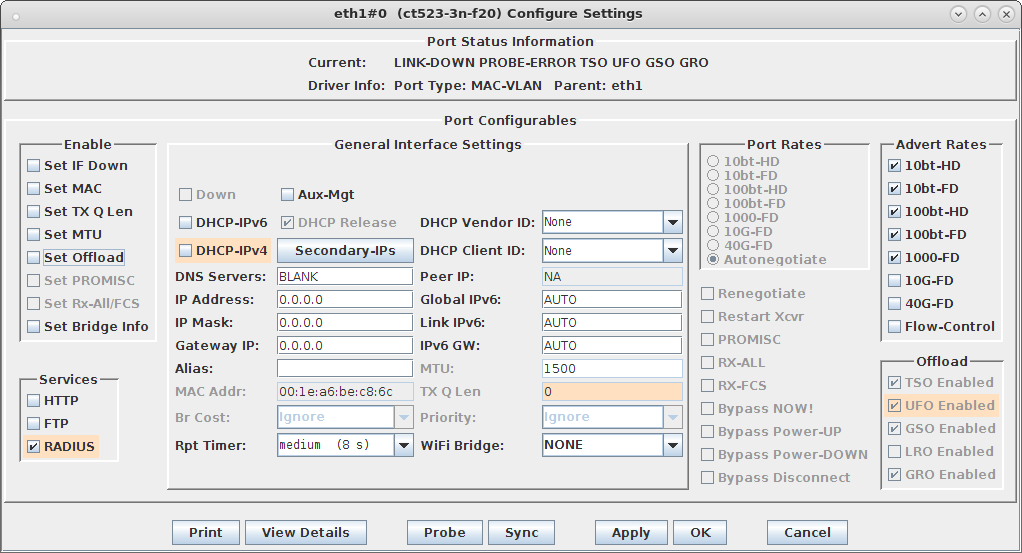
interface=eth1#0 driver=wired logger_syslog=-1 logger_syslog_level=2 logger_stdout=-1 logger_stdout_level=2 dump_file=/home/lanforge/wifi/hostapd_eth1#0.dump ctrl_interface=/var/run/hostapd ctrl_interface_group=0 ieee8021x=1 eapol_key_index_workaround=0 eap_server=1 eap_user_file=/home/lanforge/hs20/AS/hostapd-osen.eap_user server_id=ct523-3n-f20 eap_sim_db=unix:/tmp/hlr_auc_gw.sock radius_server_auth_port=1820 radius_server_clients=/home/lanforge/hs20/AS/hostap.radius_clients ca_cert=/home/lanforge/hs20/ca/ca.pem server_cert=/home/lanforge/hs20/ca/server.pem private_key=/home/lanforge/hs20/ca/server.key private_key_passwd=lanforge ocsp_stapling_response=/home/lanforge/hs20/ca/ocsp-server-cache.der
interface=eth1#1 driver=wired logger_syslog=-1 logger_syslog_level=2 logger_stdout=-1 logger_stdout_level=2 dump_file=/home/lanforge/wifi/hostapd_eth1#1.dump ctrl_interface=/var/run/hostapd ctrl_interface_group=0 ieee8021x=1 eapol_key_index_workaround=0 eap_server=1 eap_user_file=sqlite:/home/lanforge/hs20/AS/DB/eap_user.db server_id=ct523-3n-f20 eap_sim_db=unix:/tmp/hlr_auc_gw.sock db=/home/lanforge/hs20/AS/DB/eap_sim.db radius_server_auth_port=1821 radius_server_clients=/home/lanforge/hs20/AS/hostap.radius_clients ca_cert=/home/lanforge/hs20/ca/ca.pem server_cert=/home/lanforge/hs20/ca/server.pem private_key=/home/lanforge/hs20/ca/server.key private_key_passwd=lanforge ocsp_stapling_response=/home/lanforge/hs20/ca/ocsp-server-cache.der
cd /home/lanforgeNOTE: If the hlr_auc_gw does not start, you may have to remove the file /tmp/hlr_auc_gw.sock first.
. lanforge.profile
hlr_auc_gw -m /etc/hlr_auc_gw.milenage_db > /tmp/hlr_auc_gw.log &
ps auxwww |grep hostapd_eth
cat /home/lanforge/wifi/hostapd_log_eth1#0.txt cat /home/lanforge/wifi/hostapd_log_eth1#1.txt
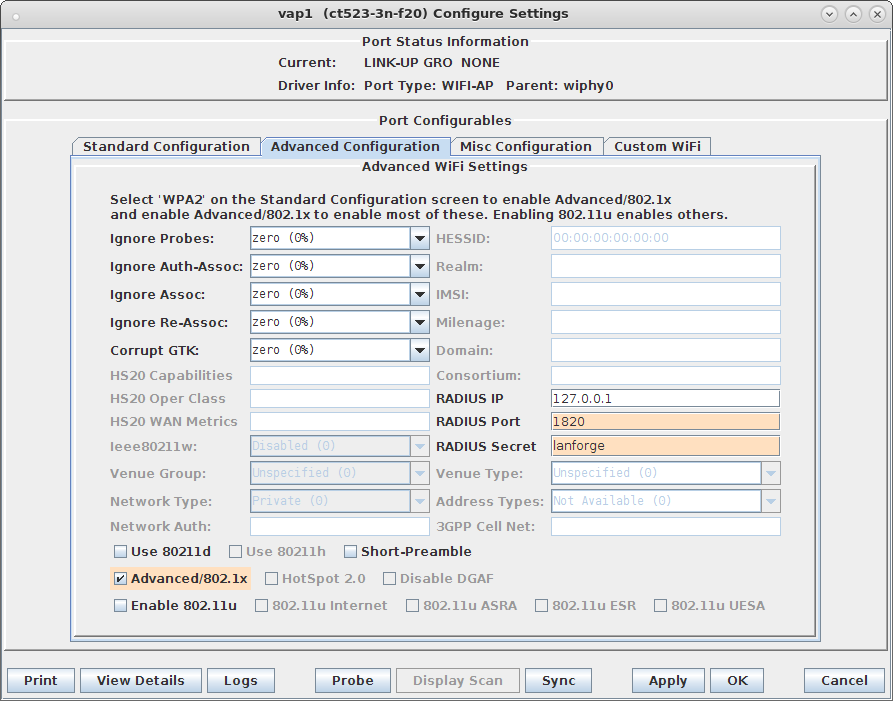
ocsp_stapling_response=/home/lanforge/hs20/ca/ocsp-server-cache.der
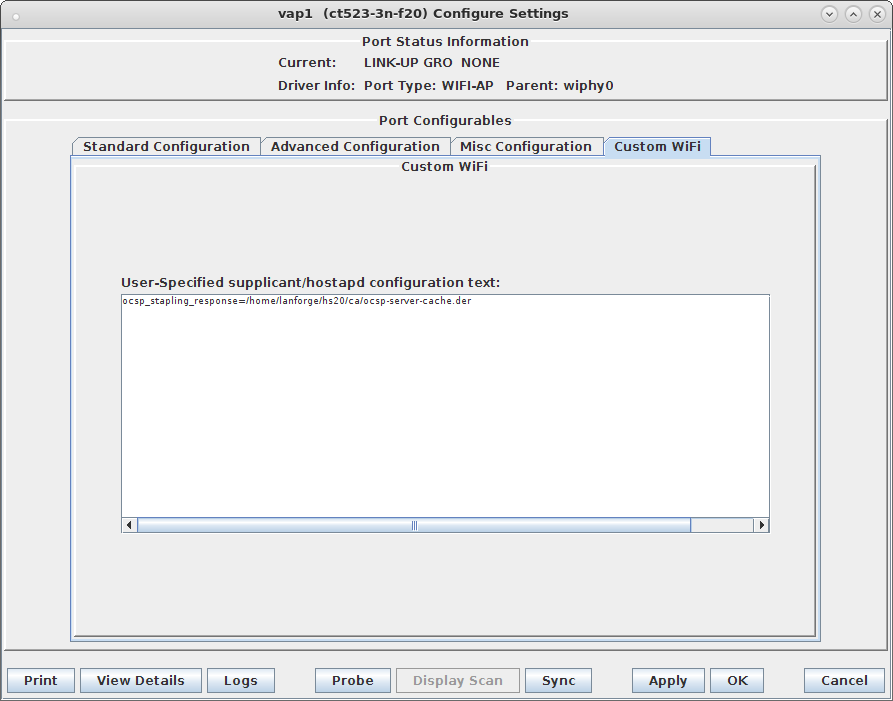
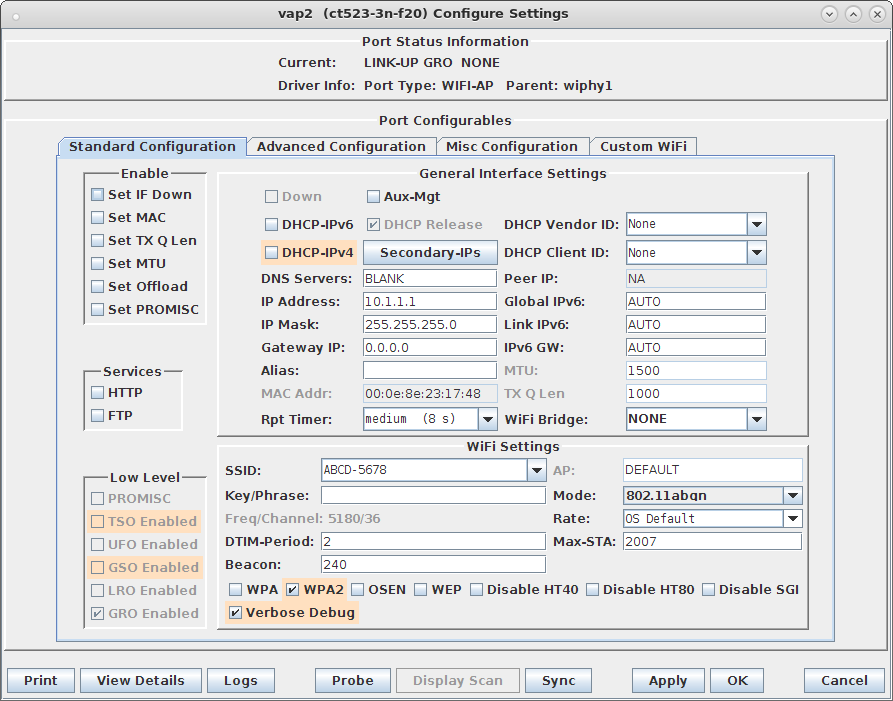
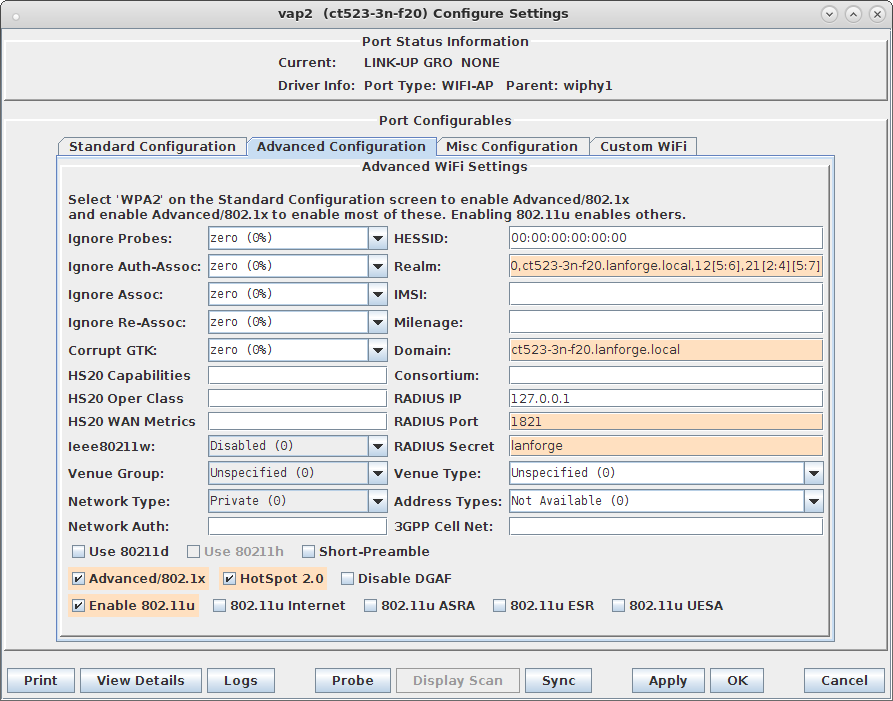
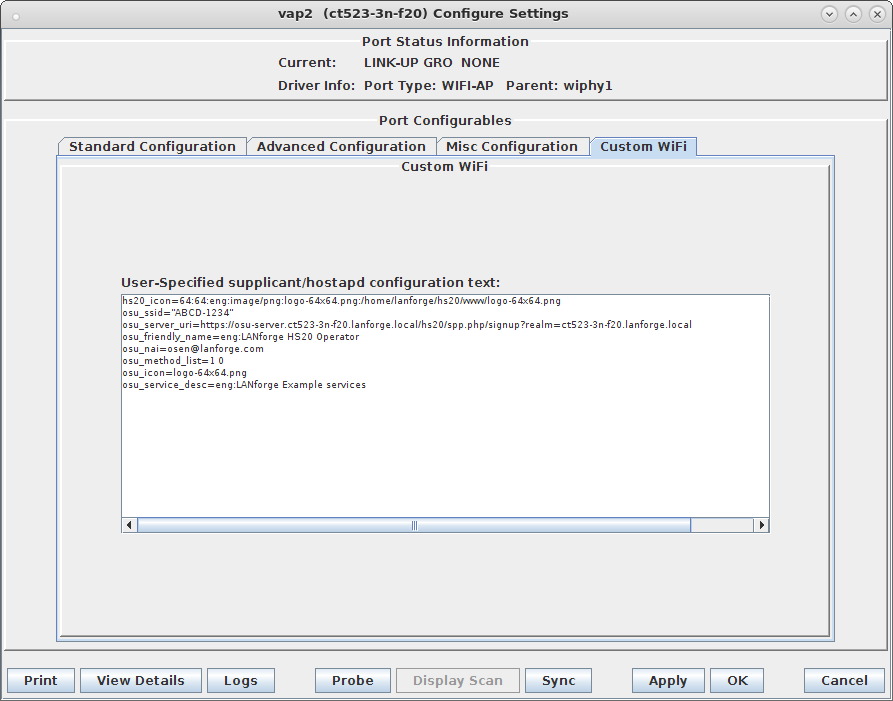
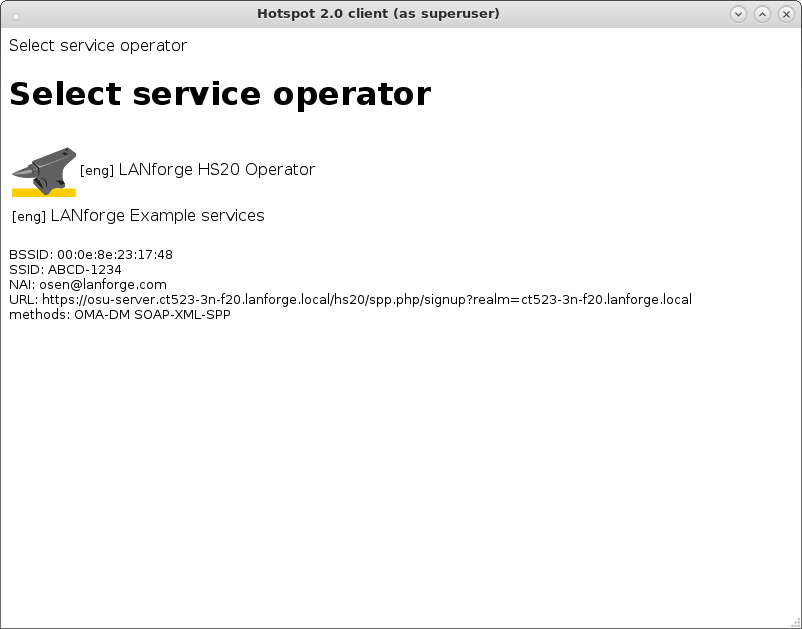
hs20_icon=64:64:eng:image/png:logo-64x64.png:/home/lanforge/hs20/www/logo-64x64.png osu_ssid="ABCD-1234" osu_server_uri=https://osu-server.ct523-3n-f20.lanforge.local/hs20/spp.php/signup?realm=ct523-3n-f20.lanforge.local osu_friendly_name=eng:LANforge HS20 Operator osu_nai=osen@lanforge.com osu_method_list=1 0 osu_icon=logo-64x64.png osu_service_desc=eng:LANforge Example services
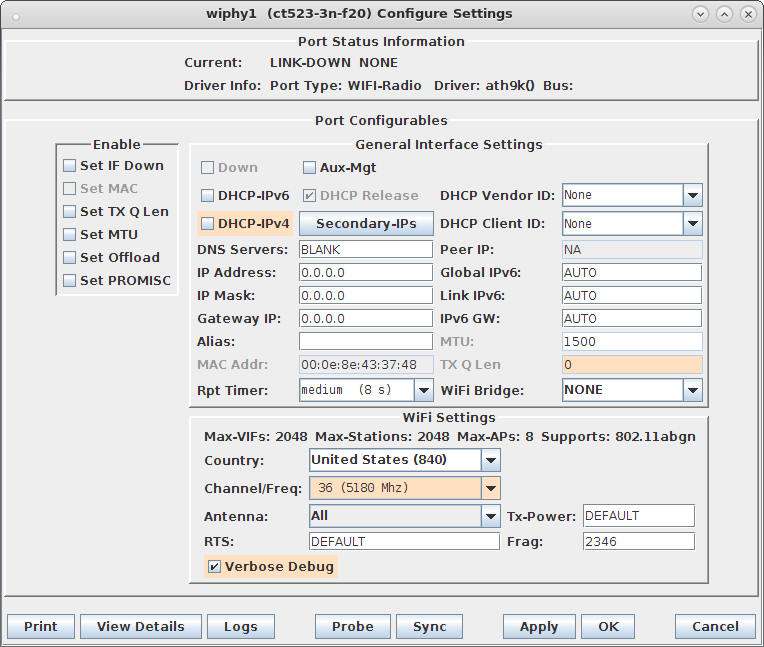
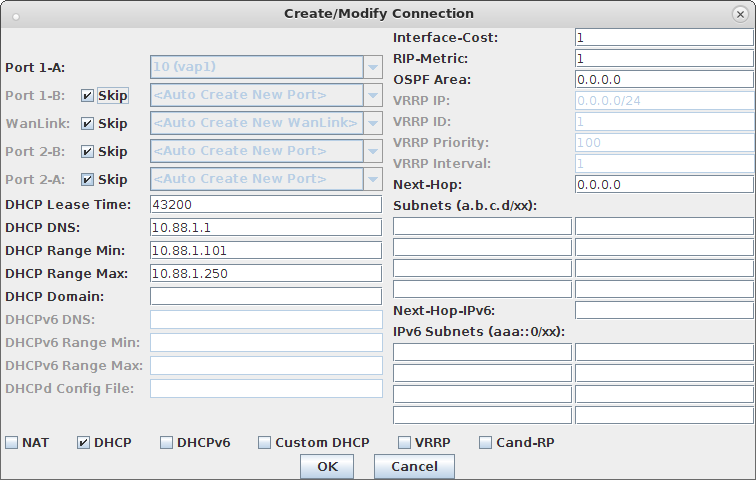
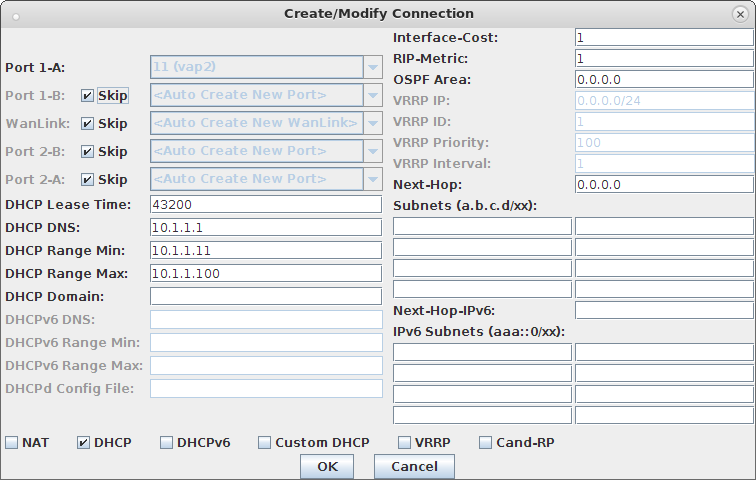
ps auxwww |grep hostapd_vap
tail -f /home/lanforge/wifi/hostapd_log_vap1.txt tail -f /home/lanforge/wifi/hostapd_log_vap2.txt
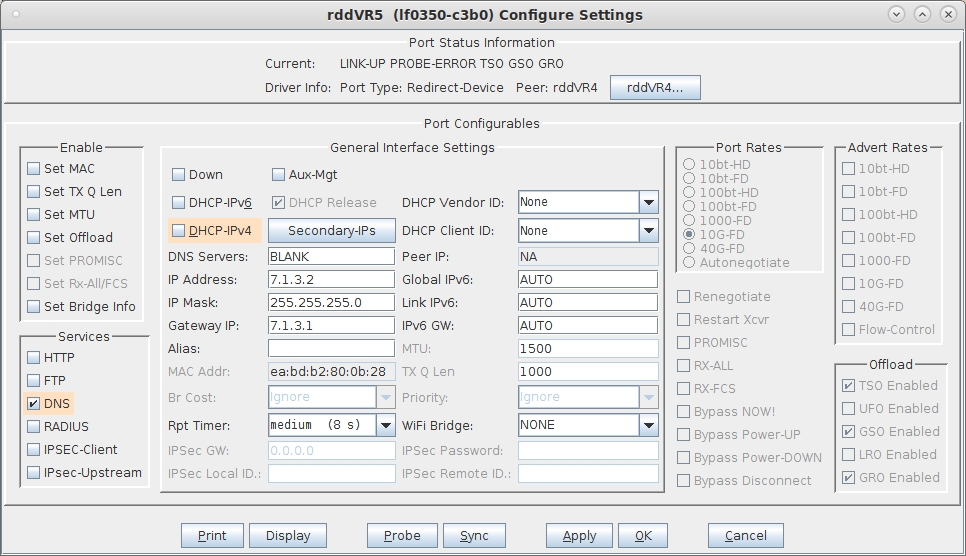
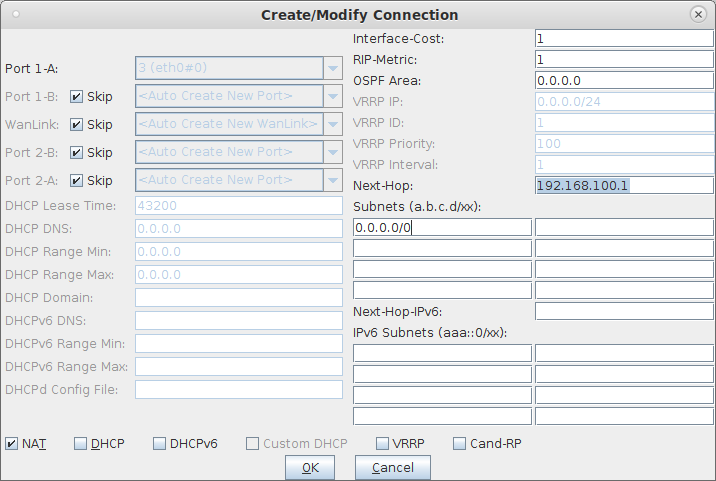
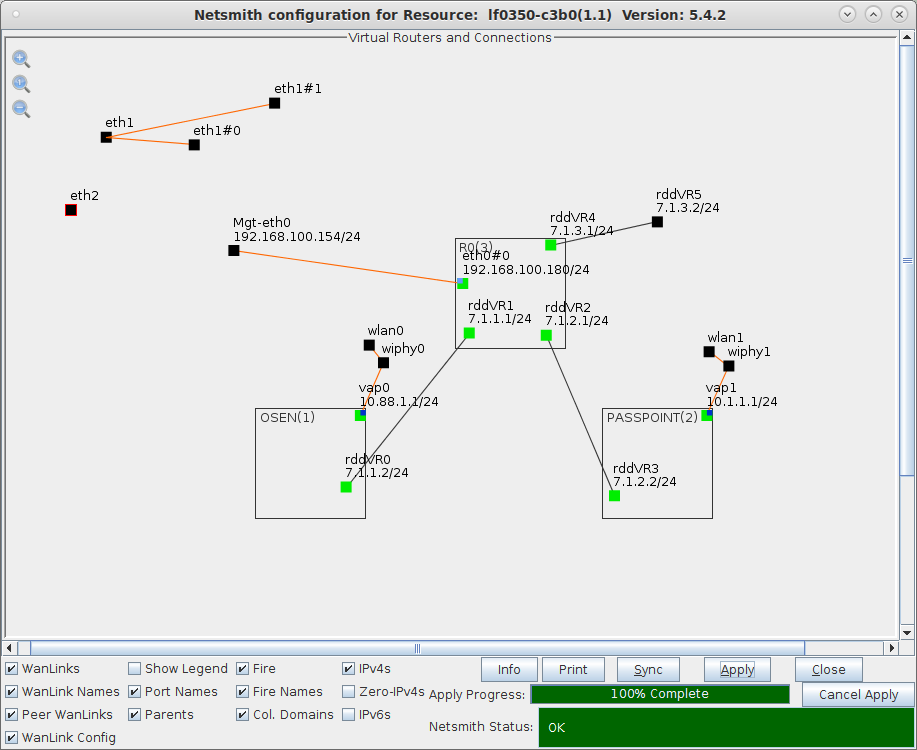
For more information see WiFi Testing: Configuring a Virtual AP with Limited Stations
, Virtual Router with NAT Cookbook , Virtual Router with DHCP Cookbook###LANFORGE-HOSTS-START### # This section may be over-written by lf_kinstall.pl 127.0.0.1 osu-client.lf0350-c3b0.lanforge.local 10.88.1.1 osu-server.lf0350-c3b0.lanforge.local 127.0.0.1 osu-revoked.lf0350-c3b0.lanforge.local 10.88.1.1 osu-signup.lf0350-c3b0.lanforge.local 7.1.3.2 ocsp.lf0350-c3b0.lanforge.local ###LANFORGE-HOSTS-STOP### ###-LF-HOSTAME-NEXT-### 192.168.100.154 lf0350-c3b0 lanforge-srv
su - root cd /home/lanforge . lanforge.profile vrf_exec.bash rddVR5 ./ocsp.bash > /dev/null 2>&1 &
vrf_exec.bash vap0 httpd -f /etc/httpd/conf/httpd-hs20.conf
<DevInfo xmlns="urn:oma:mo:oma-dm-devinfo:1.0">
<DevId>urn:Example:HS20-station:123456</DevId>
<Man>Manufacturer</Man>
<Mod>HS20-station</Mod>
<DmV>1.2</DmV>
<Lang>en</Lang>
</DevInfo>
<DevDetail xmlns="urn:oma:mo:oma-dm-devdetail:1.0">
<Ext>
<org.wi-fi>
<Wi-Fi>
<EAPMethodList>
<EAPMethod1>
<EAPType>13</EAPType>
</EAPMethod1>
<EAPMethod2>
<EAPType>21</EAPType>
<InnerMethod>MS-CHAP-V2</InnerMethod>
</EAPMethod2>
<EAPMethod3>
<EAPType>18</EAPType>
</EAPMethod3>
<EAPMethod4>
<EAPType>23</EAPType>
</EAPMethod4>
<EAPMethod5>
<EAPType>50</EAPType>
</EAPMethod5>
</EAPMethodList>
<ManufacturingCertificate>false</ManufacturingCertificate>
<Wi-FiMACAddress>020102030405</Wi-FiMACAddress>
<IMSI>310026000000000</IMSI>
<IMEI_MEID>imei:490123456789012</IMEI_MEID>
<ClientTriggerRedirectURI>http://localhost:12345/</ClientTriggerRedirectURI>
<Ops>
<launchBrowserToURI></launchBrowserToURI>
<negotiateClientCertTLS></negotiateClientCertTLS>
<getCertificate></getCertificate>
</Ops>
</Wi-Fi>
</org.wi-fi>
</Ext>
<URI>
<MaxDepth>0</MaxDepth>
<MaxTotLen>0</MaxTotLen>
<MaxSegLen>0</MaxSegLen>
</URI>
<DevType>MobilePhone</DevType>
<OEM>Manufacturer</OEM>
<FwV>1.0</FwV>
<SwV>1.0</SwV>
<HwV>1.0</HwV>
<LrgObj>false</LrgObj>
</DevDetail>
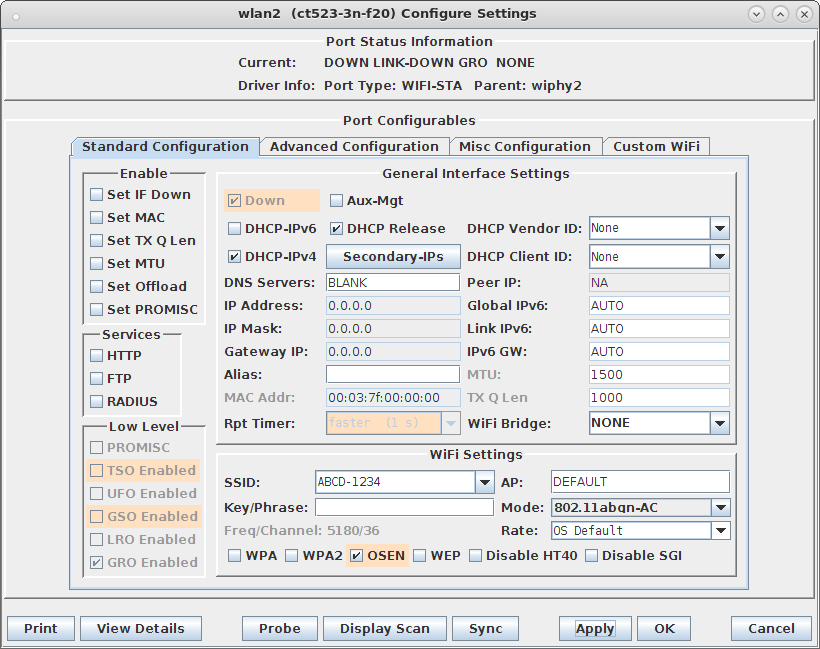
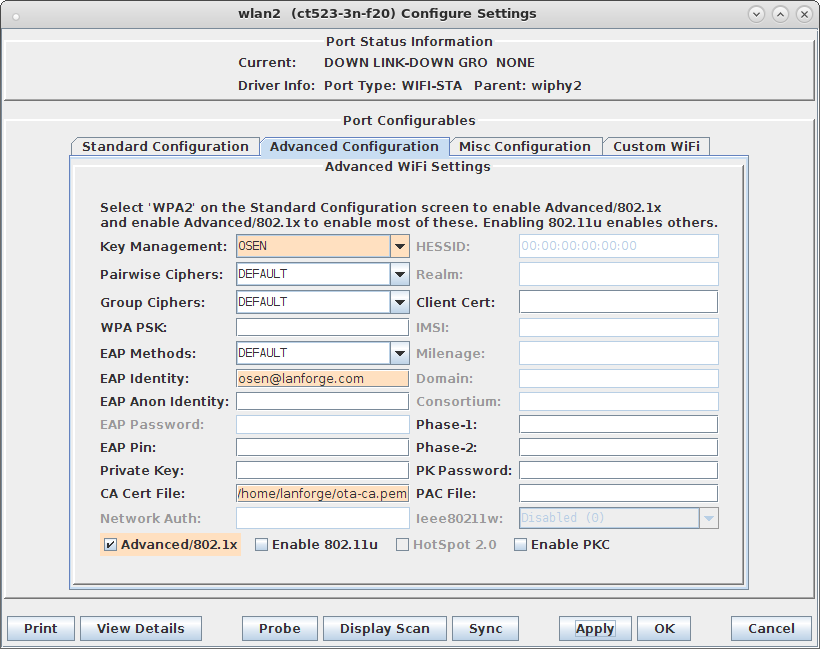
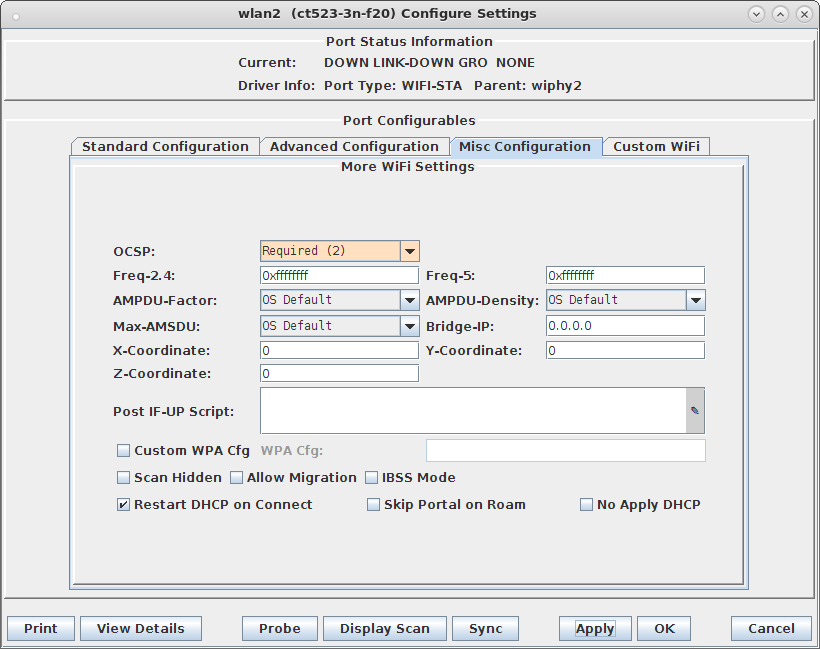
cd /home/lanforge/wifi/osu_wlan2 LD_PRELOAD=/home/lanforge/local/lib/resolvconf-override.so NAMESERVER1=7.1.3.2 \ vrf_exec wlan2 ~lanforge/local/hs20/client/hs20-osu-client -x /home/lanforge/local/hs20/spp/spp.xsd -dd -S wlan2 signup
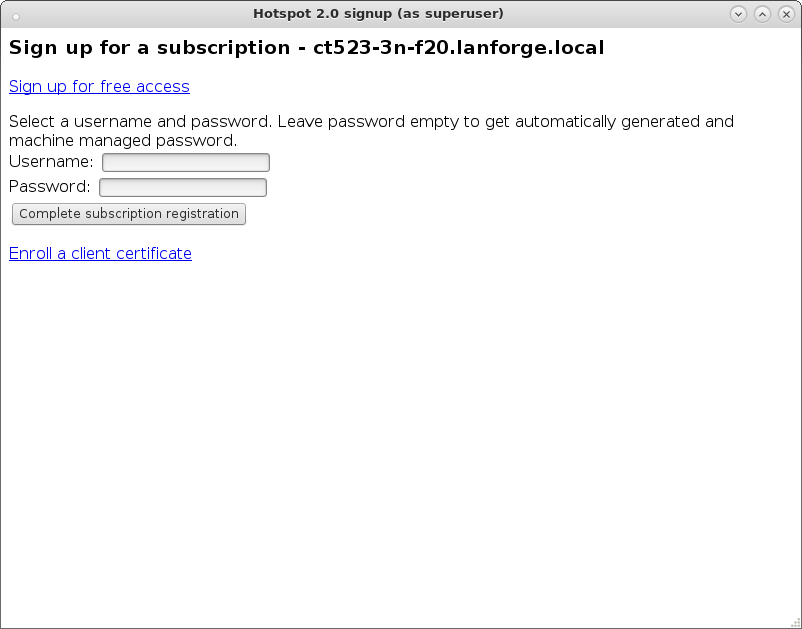
cd /home/lanforge/wifi/osu_wlan2 rm -rf SP