|
|
||
| Network Testing and Emulation Solutions |
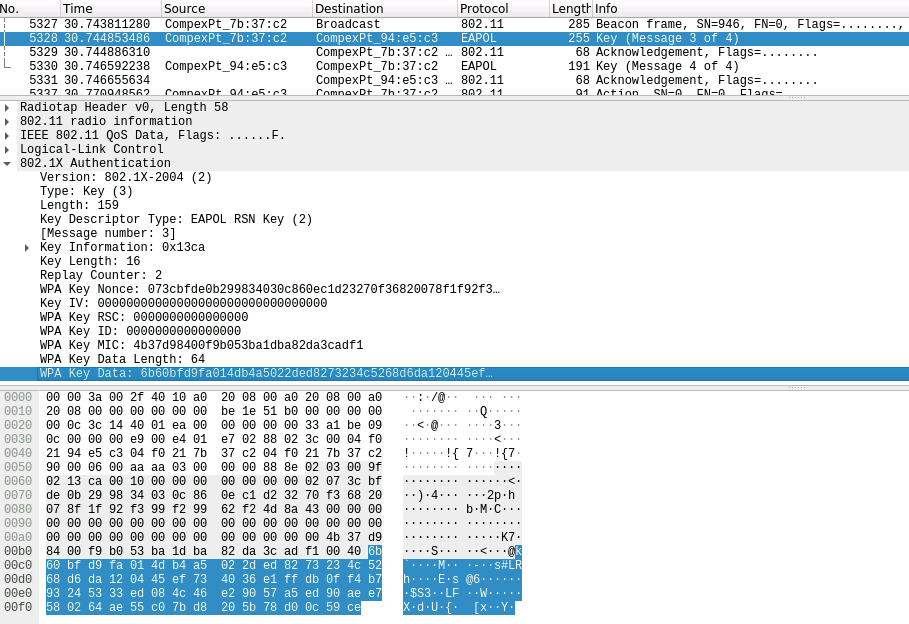
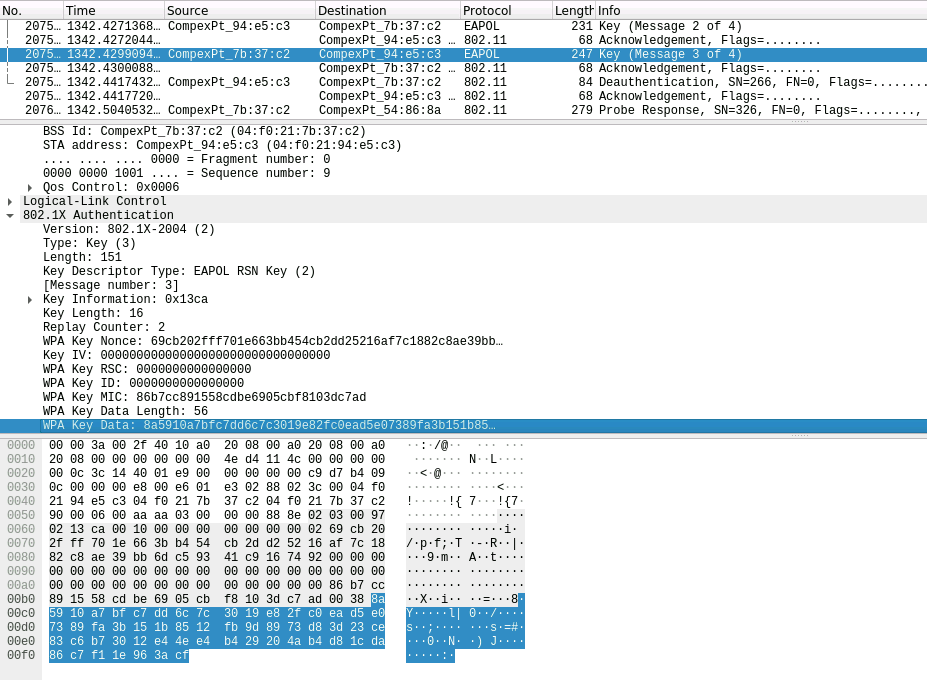
| In this test scenario a LANforge system acts as a WiFi access point configured to use WPA2 authentication. The rsne_override_eapol field in LANforge Custom WiFi Parameters provides means to corrupt or customize certain information elements (IEs) in the third of four messages comprising EAPOL authentication "handshake". These IEs contain information about RSN encryption, including Pre-Shared Key (PSK) information required by 802.11 protocol for authentication success. Thus, such IEs may be overriden for the purpose of testing behavior under faulty authentication. Listed below is an example test case, of which documentation may be found in the hostap repository. | |
For more information see Create VAP in Bridge Mode
For more information see Generating Traffic for WLAN Testing
For more information see WPA2-Authentication Test Scenario
For more information see Using Wireshark to Sniff WiFi Monitors
Control (No Change):