|
|
||
| Network Testing and Emulation Solutions |
| Using the realm.py library we will write a script that will allow us to automate the creation of stations and Layer-3 cross connects. We will also be able to start and stop traffic over the cross connects using the script. We will be referencing the script, test_ipv4_variable_time.py, as an example throughout this cookbook. Requires LANforge 5.4.2. | |
import sys. Then useif 'py-json' not in sys.path: sys.path.append(os.path.join(os.path.abspath('..'), 'py-json'))
from LANforge.lfcli_base import LFCliBase
station_list = LFUtils.port_name_series(prefix_="sta",
start_id_=0,
end_id_=4,
padding_number_=10000)
ip_var_test = IPV4VariableTime(lfjson_host, lfjson_port,
number_template="00",
sta_list=station_list,
name_prefix="var_time",
ssid="testNet",
password="testPass",
resource=1,
security="wpa2",
test_duration="5m",
side_a_min_rate=256,
side_b_min_rate=256)
def main():
lfjson_host = "localhost"
lfjson_port = 8080
station_list = LFUtils.portNameSeries(prefix_="sta", start_id_=0, end_id_=4, padding_number_=10000)
ip_var_test = IPV4VariableTime(lfjson_host, lfjson_port, number_template="00", sta_list=station_list,
name_prefix="var_time",
ssid="testNet",
password="testPass",
resource=1,
security="wpa2", test_duration="5m",
side_a_min_rate=256, side_b_min_rate=256),
ip_var_test.cleanup(station_list)
ip_var_test.build()
if not ip_var_test.passes():
print(ip_var_test.get_fail_message())
exit(1)
ip_var_test.start(False, False)
ip_var_test.stop()
if not ip_var_test.passes():
print(ip_var_test.get_fail_message())
exit(1)
time.sleep(30)
ip_var_test.cleanup(station_list)
if ip_var_test.passes():
print("Full test passed, all connections increased rx bytes")
get_result_list()
get_failed_result_list()
get_fail_message()
get_all_message()
station_profile.use_security()
station_profile.set_number_template() to name our stations
self.station_profile.set_command_flag("add_sta","create_admin_down",1)
self.station_profile.set_command_param("set_port","report_timer",1500)
self.station_profile.set_command_flag("set_port","rpt_timer", 1)
for station in range(len(self.sta_list)):
temp_sta_list.append(str(self.resource)+"."+self.sta_list[station])
self.station_profile.create(resource=1, radio="wiphy0", sta_names_=self.sta_list, debug=False)
self.cx_profile.create(endp_type="lf_udp", side_a=temp_sta_list, side_b="1.eth1", sleep_time=.5)
self._pass("PASS: Station build finished")
self.station_profile.use_security(security_type, ssid, passwd) is the preferred method to use when setting the security type, ssid, and password variablesself.station_profile.use_security("wpa2", "testNet", "testPass")
self.station_profile.number_template_="00"
self.station_profile.mode=0
self.cx_profile.name_prefix="test_"
self.cx_profile.side_a_min_bps=56000
self.cx_profile.side_b_min_bps=56000
key_mgmt="WPA-EAP"We can then use these variables to call the set_wifi_extra() method
eap="TTLS"
identity="testuser"
passwd="testpasswd"
realm="localhost.localdomain"
domain="localhost.localdomain"
hessid="00:00:00:00:00:01"
station_profile.set_wifi_extra(key_mgmt, eap, identity, passwd, realm, domain, hessid)
_debug_on=True in StationProfile.create()
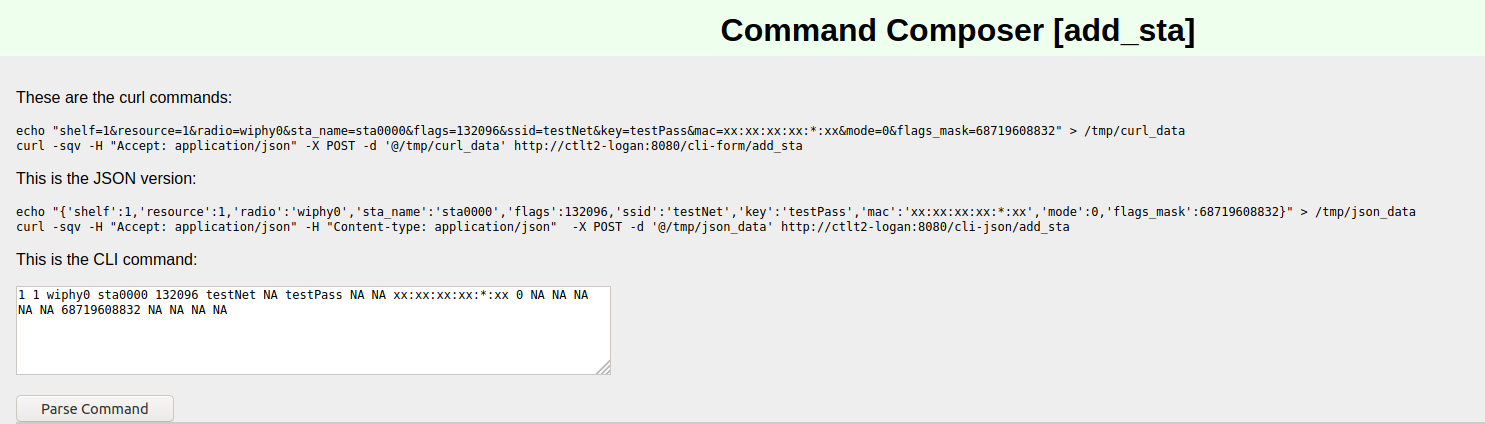
- 381 - sta0000- - - - - - - - - - - - - - - - - -
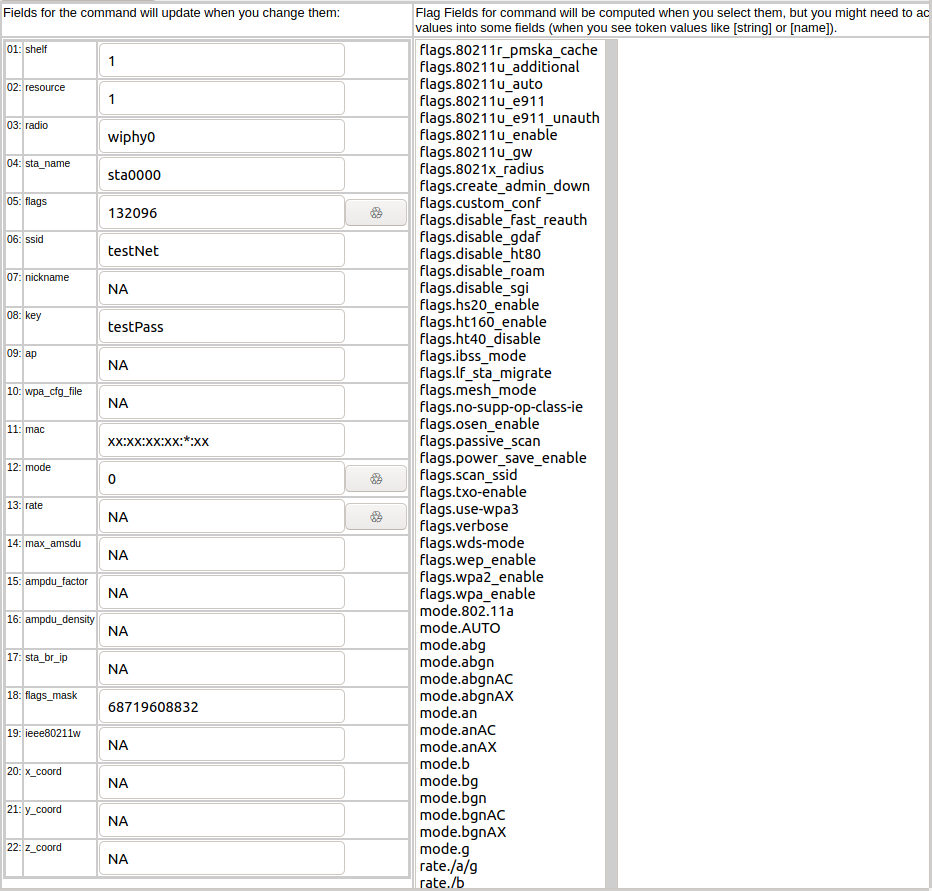
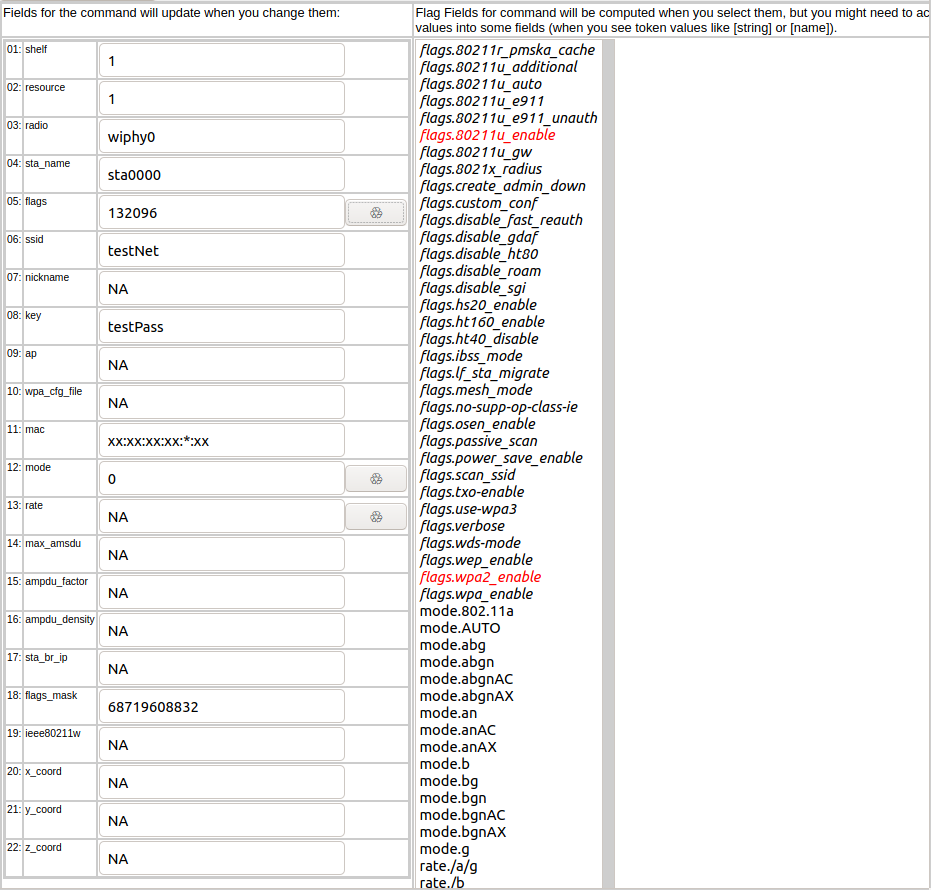
{'flags': 132096,
'flags_mask': 68719608832,
'key': 'testPass',
'mac': 'xx:xx:xx:xx:*:xx',
'mode': 0,'
radio': 'wiphy0',
'resource': 1,
'shelf': 1,
'ssid': 'testNet,
'sta_name': 'sta0000'}
{'current_flags': 2147483649,
'interest': 8437762,
'port': 'sta0000',
'report_timer': 1500,
'resource': 1,
'shelf': 1}
<LANforge.LFRequest.LFRequest object at 0x7f13dbc56850>
-~381 - - - - - - - - - - - - - - - - - - -